Free security services
AWS Shield Standard (DDoS Mitigation)
Protection against the most common DDoS Attacks (such as SYN/UDP Floods, Reflection Attacks. Layer 3 and 4).
Available to all the customers without additional cost, activated by default.
Detection and mitigation is automatic.
https://aws.amazon.com/shield/
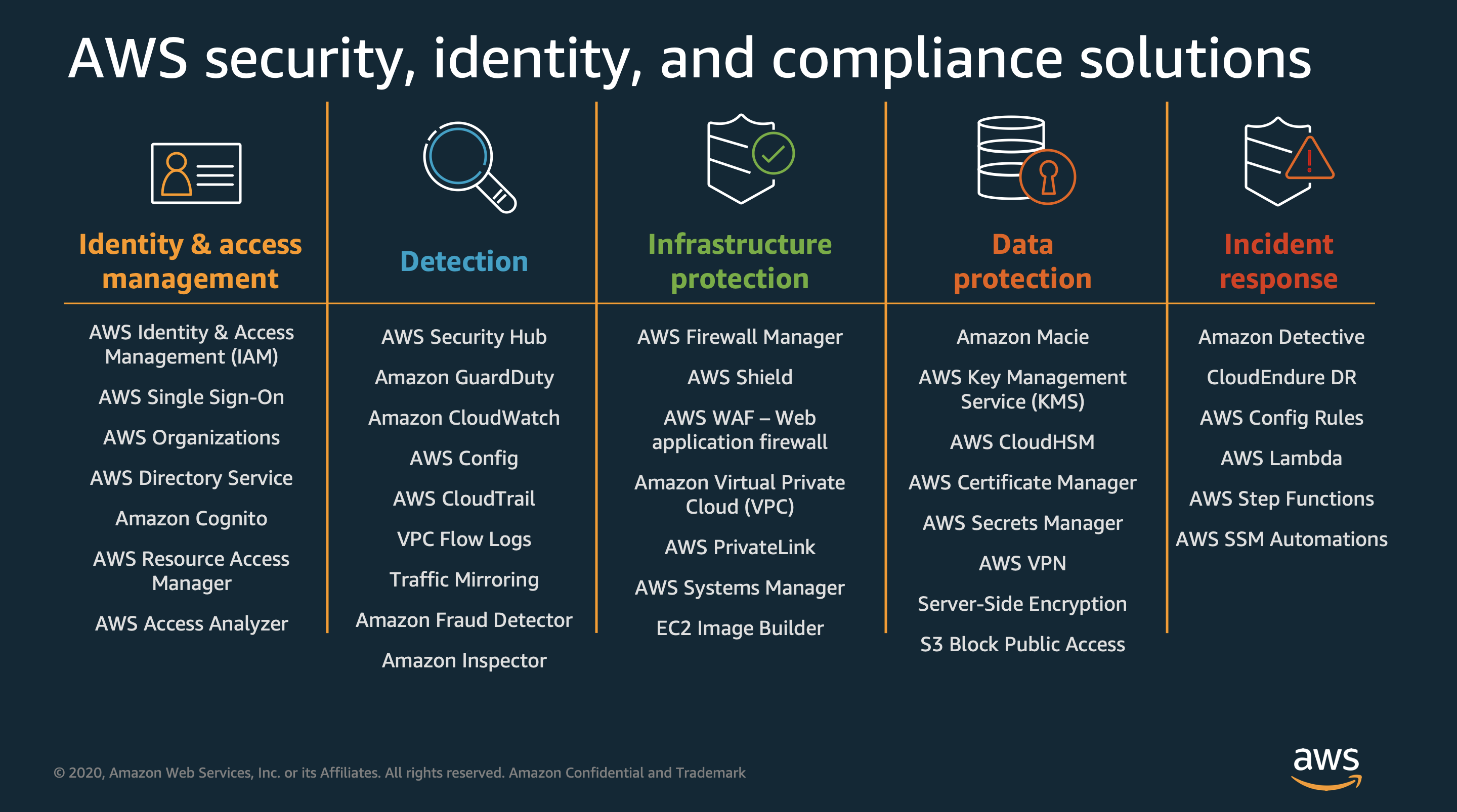
IAM
Identity and Access Management of the AWS infrastructure, granular control and enabling virtul MFA is free.
https://aws.amazon.com/iam/
IAM Access Analyzer
AWS offers free of charge this tool that uses Automated Reasoning to detect human mistakes in the configuration of policies, such as external actors (Principals) with permissions granted by resource policies such as Bucket Policies, Key Policies, etc.
https://aws.amazon.com/iam/features/analyze-access/
AWS Organizations
AWS Organizations allows you to generate a Multi-Account structure with centralized billing and gives the organization the possibility to limit the maximum permissions available for the whole organization, for a particular Business Unit, or for a specific account (with Service Control Policies)
https://aws.amazon.com/organizations/
AWS SSO
AWS SSO is a service that allows to centralize the access to multiple accounts offering a portal that allows accessing to multiple AWS Accounts with different roles and other 3rd party corporate applications. Allows the usage of an internal user repository or you can use an external directory such as AWS Directory Services, AD on-prem, or an external identity provider such as Okta, PingIdentity, OneLogin, AzureAD. AWS SSO allows access to the AWS Console and to the AWS CLI and grants temporary credentials (according to best practices).
https://aws.amazon.com/single-sign-on/
S3 Block Public Access
The Amazon S3 Block Public Access feature provides settings for access points, buckets, and accounts to help you manage public access to Amazon S3 resources. By default, new buckets, access points, and objects don’t allow public access. https://aws.amazon.com/s3/features/block-public-access/ https://docs.aws.amazon.com/AmazonS3/latest/userguide/access-control-block-public-access.html
AWS Systems Manager: Patch Manager
Note: it’s free for EC2 Instances in the AWS Cloud, for servers on-prem or multicloud it has associated costs. Patch Manager, a capability of AWS Systems Manager, automates the process of patching managed nodes with both security related and other types of updates. You can use Patch Manager to apply patches for both operating systems and applications. https://docs.aws.amazon.com/systems-manager/latest/userguide/systems-manager-patch.html
AWS Systems Manager: Session Manager
The service allows you to connect to Linux or Windows instances (powershell) to manage them through a command interface. It does not require the opening of security groups to management ports or the use of bastions. Optionally, it allows to record the executed commands and their response in text files. By integrating with AWS Console Authentication, it enables configuration of MFA for instance access.
AWS Systems Manager: Fleet Manager
The service allows you to manage instances running on AWS or on-prem servers, through a unified interface that allows you to see the health and performance of your server fleet from a console. It also allows you to collect information from the nodes to solve problems or management tasks directly from the AWS console. It includes the ability to connect to Windows instances using Remote Desktop Protocol (RDP), view folder and file contents, manage the windows registry, manage operating system users, and more. https://docs.aws.amazon.com/systems-manager/latest/userguide/fleet.html
AWS Trusted Advisor
https://aws.amazon.com/premiumsupport/technology/trusted-advisor/ https://docs.aws.amazon.com/awssupport/latest/user/trusted-advisor.html
EC2 Image Builder (Golden Images)
(the service is free, only the generated infrastructure incurs in costs)
AWS CloudFormation (Infrastructure as Code)
(the service is free, only the generated infrastructure incurs in costs)