IAM Roles: Least Privilege Review
IAM Policy Review
Periodic review of your IAM roles is recommended to ensure that they grant the minimum privileges required for the function to perform (least privilege)
https://docs.aws.amazon.com/es_es/IAM/latest/UserGuide/best-practices.html#grant-least-privilege
Unintended access review
In particular, review asterisks in policies: … “Action”: “service-prefix": “*” … or … “Resource”: “*” …
Frequently when these broad permits are granted it is due to lack of dedication/effort in the construction of a more specific IAM policy.
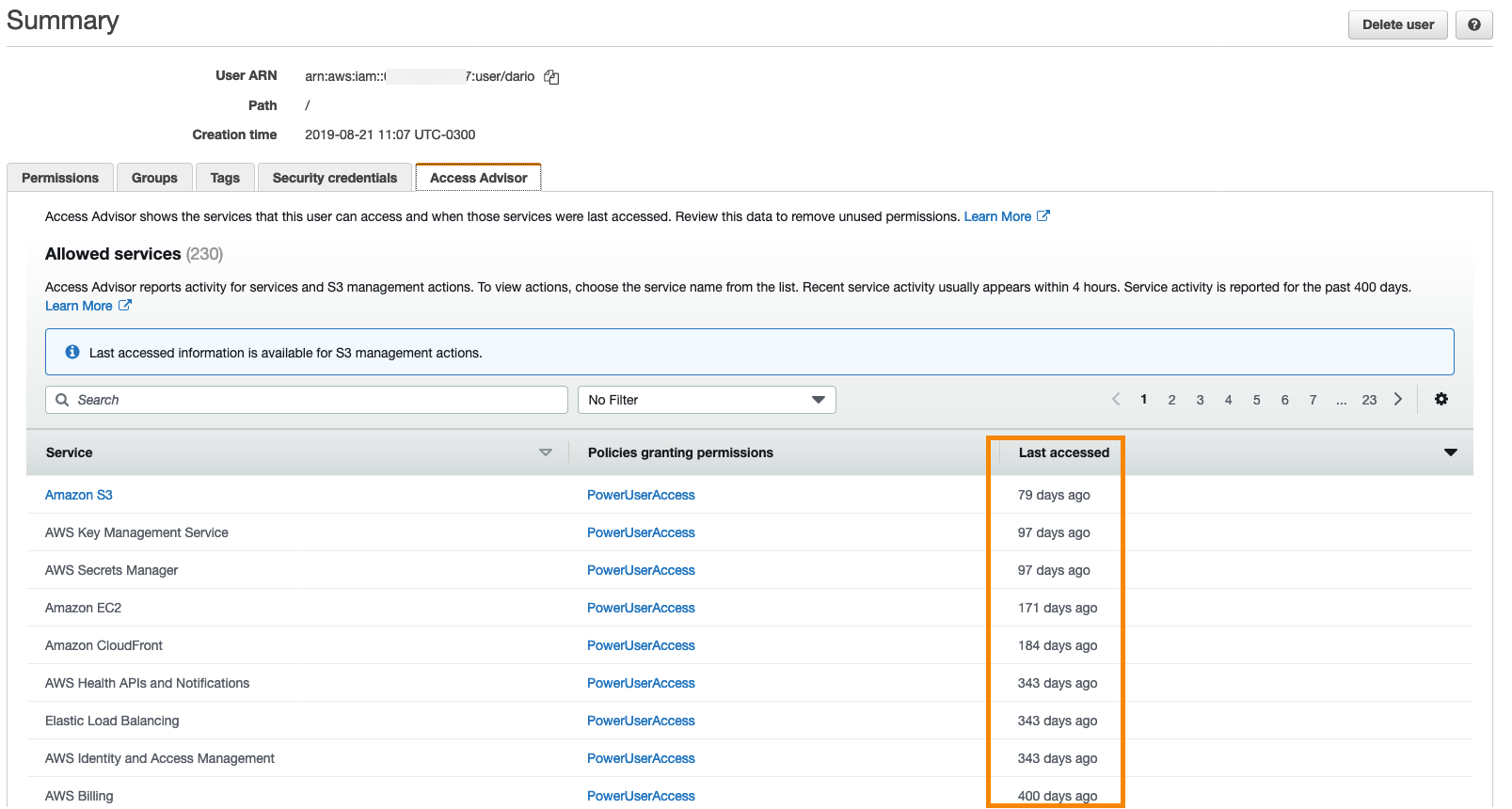
IAM Access Advisor
Use IAM Access Advisor
to identify unused access:
IAM Access Analyzer - Policy generation
IAM Access Analyzer has a policy generation capability based on user activity (as reflected on AWS Cloudtrail). Use this functionality to refine policies with excessive permissions, not used in a significant period of time (which will depend on its use case).
https://docs.aws.amazon.com/IAM/latest/UserGuide/access-analyzer-policy-generation.html
Policy examples:
https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_examples.html