Manage your instances with AWS Systems Manager Fleet Manager
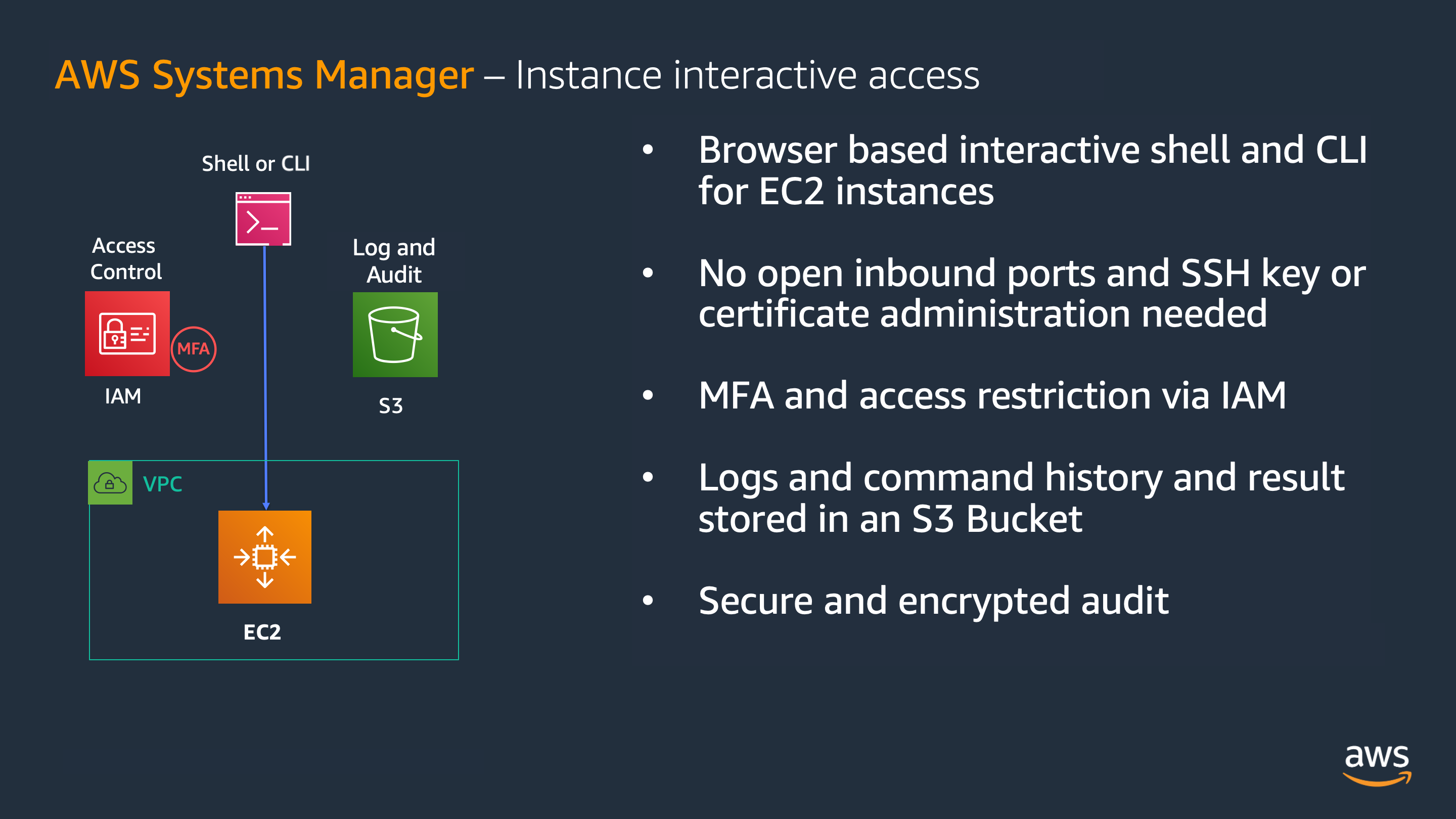
We recommend that you use AWS Systems Manager Session Manager to manage your instances instead of directly accessing via SSH because you don’t need to open ports in Security Groups, it allows MFA, and it provides command history auditing. In Windows instances, it is also possible to use AWS Systems Manager Session Manager to gain PowerShell access, but if a graphical interface access is required, it is recommended to use hardened bastion hosts, thus reducing exposure by limiting the number of entry points.
Accessing your instances to perform administrative tasks
It’s not advisable to expose the administration ports of your instances (RDP 3389 and SSH 22) to internet, adversaries could try to leverage a vulnerability to access and take control, or they could achieve access thru brute force attacks.
Previously we used to recommend the use of bastion hosts, which were hardened instances with security features to mitigate the risk of having that instance exposed. A best practice about the use of bastion has always been restricting the access from certain IPs whenever possible.
The use of Bastion hosts is better than granting direct access to the instances opening their RDP/SSH ports, however, curently there is a better way, using AWS Systems Manager.
AWS Systems Manager Fleet Manager and Session Manager
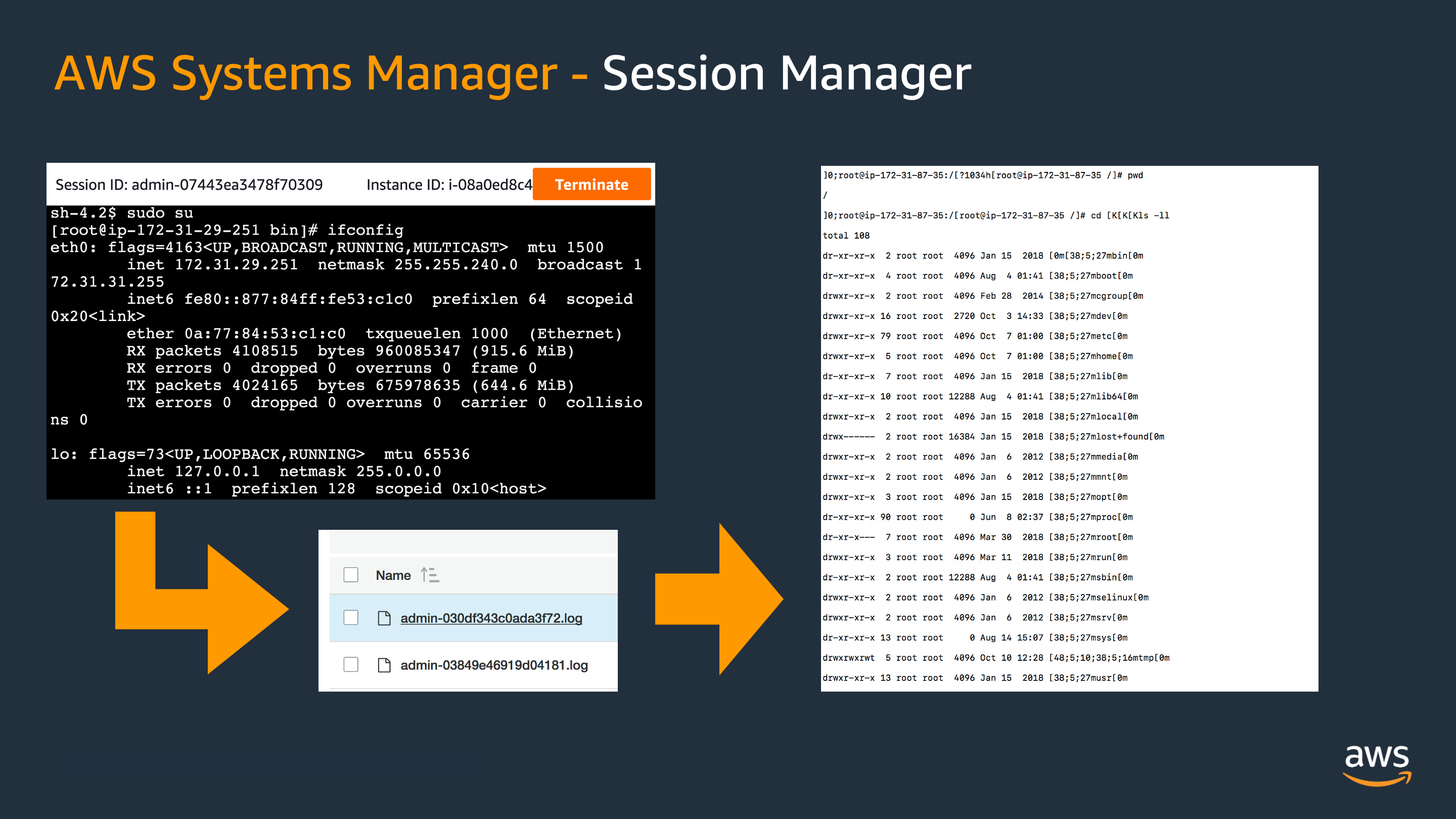
It’s recommended to use AWS Systems Manager (SSM) Session Manager to access instances instead using SSH as it does not require to open ports in the security groups (the connection is outgoing from the instance towards the Systems Manager endpoint, and it’s initiated by te agent), also it’s possible to configure MFA for accessing to the console (on AWS IAM Identity Center (succesor to AWS Single Sign-On) or in the IAM user), and the service allows (optionally) enabling audit logs on the commands executed.
For Windows instances you can use AWS Sytems Manager Fleet Manager, that among its multiple features, it allows managing the instances using Remote Desktop (RDP) without the need to open port 3389 as the conection is initiated from the agent. Leveraging it’s integration with AWS IAM Identity Center (succesor to AWS Single Sign-On) you can log in to Windows instances with one click, and without providing additional credentials.