Home > Quick Wins > Enable, Centralize, and Secure AWS CloudTrail Logs
Enable, Centralize, and Secure AWS CloudTrail Logs
It is advisable to use AWS CloudTrail audit logs to investigate incidents by setting them to retain the logs for the period that your security policy determines. It is also recommended to centralize them into a Logging account to protect them from malicious access, or if you use a single account, control access to those logs using IAM policies.
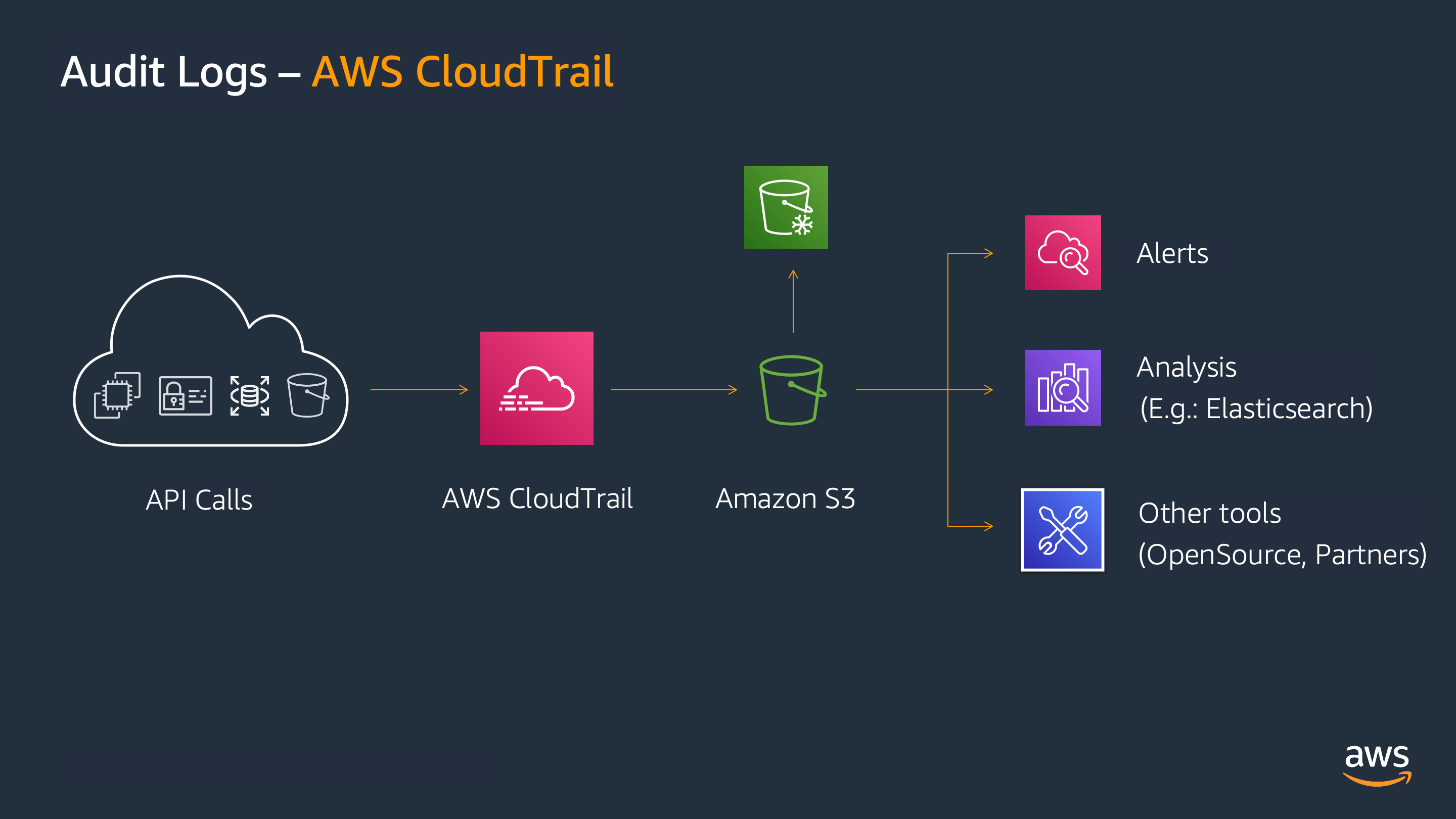
If you use AWS Control Tower for Multi-Account Management , the Logging account is generated, where the logs are automatically centralized and protected.
AWS CloudTrail Mindmap
https://www.xmind.net/m/sY4HG3
Pricing
https://aws.amazon.com/cloudtrail/pricing
Management event activity that AWS CloudTrail recorded during the last 90 days can be viewed and filtered for free through the AWS CloudTrail console or using the AWS CLI.