Advanced WAF protection with Custom Rules
Protect your applications with custom rules using AWS WAF
As we previously saw ( here ) you can quickly and easily implement general application protection rules leveraging AWS WAF managed rules, however, there are some protections that are specific to each application, for example the limit of allowed requests every 5 minutes (rate limiting) from a single IP address, or some specific protection related to a vulnerability detected.
AWS WAF allows the incorporation of custom rules that you can build with the interface, or via JSON, and the rules created using the interface can be exported as JSON to send them to a version control system.
Virtual Patching
Once a vulnerability is detected in an application, it must be remedied in the code, and if it is not possible, or would take a long time, it is recommended to implement custom rules to protect vulnerable applications while these errors are fixed.
For example, if it is detected that the lack of sanitization in a code allows an SQL injection attacks, the forms submission (post) could be denied where an apostrophe is found (’).
Rate limiting
In addition, it is advisable to configure rate limits according to the amount of requests expected in the application, since it reduces the probability of many potential attacks, such as Layer 7 DDoS attacks like HTTP Flood, Bot attacks like Credential Stuffing, and reconnaissance activities.
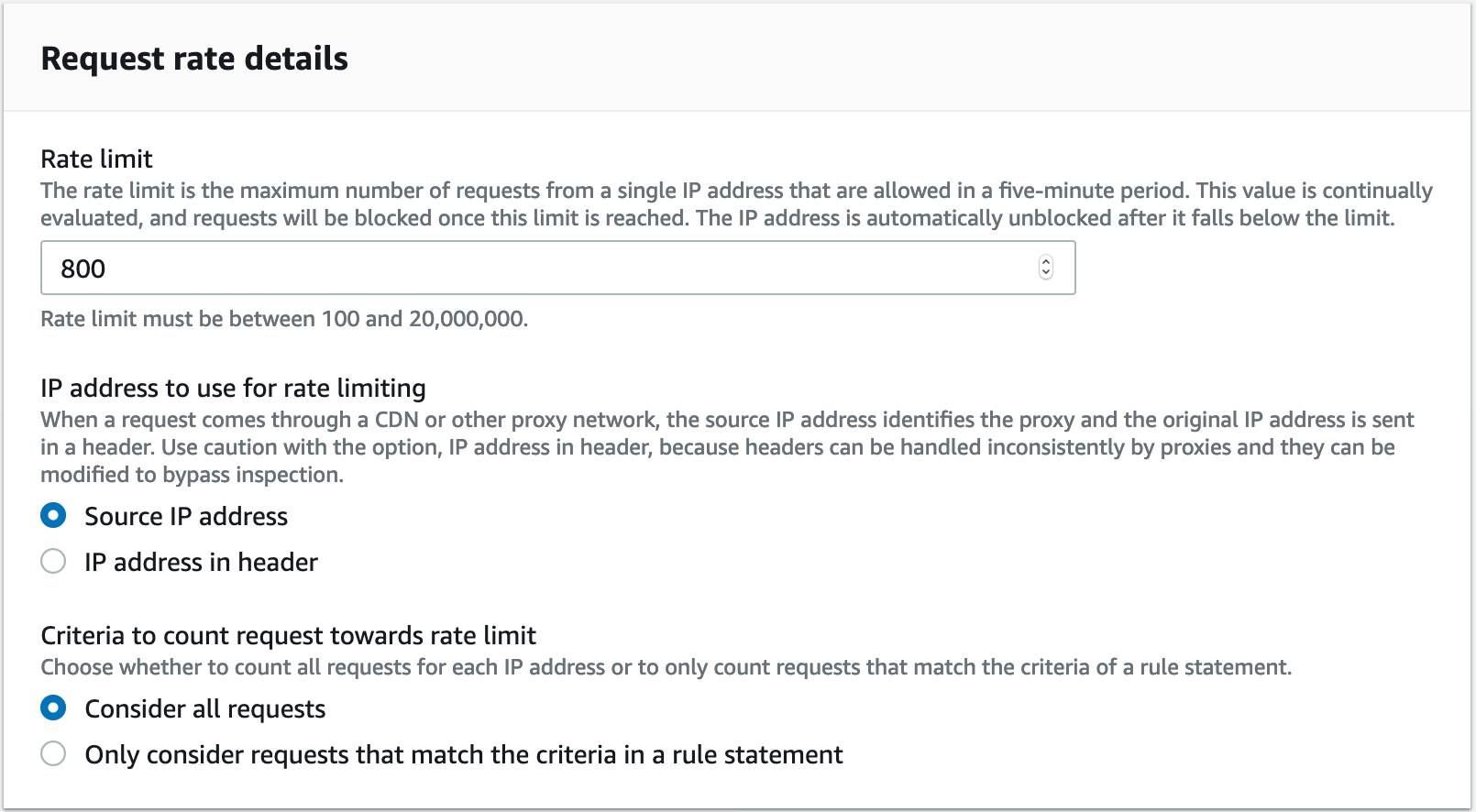
You are advised to set up a amount based on monitoring, or establishing a fixed limit in “Count” mode initially and evaluate that the normal usage of the application does not go beyond those thresholds, and after you have tuned the number to avoid triggering the rule on normal usage, then you switch it to block mode:
It’s also possible to set up rate limits specifically for requests that come from countries where traffic is not expected:
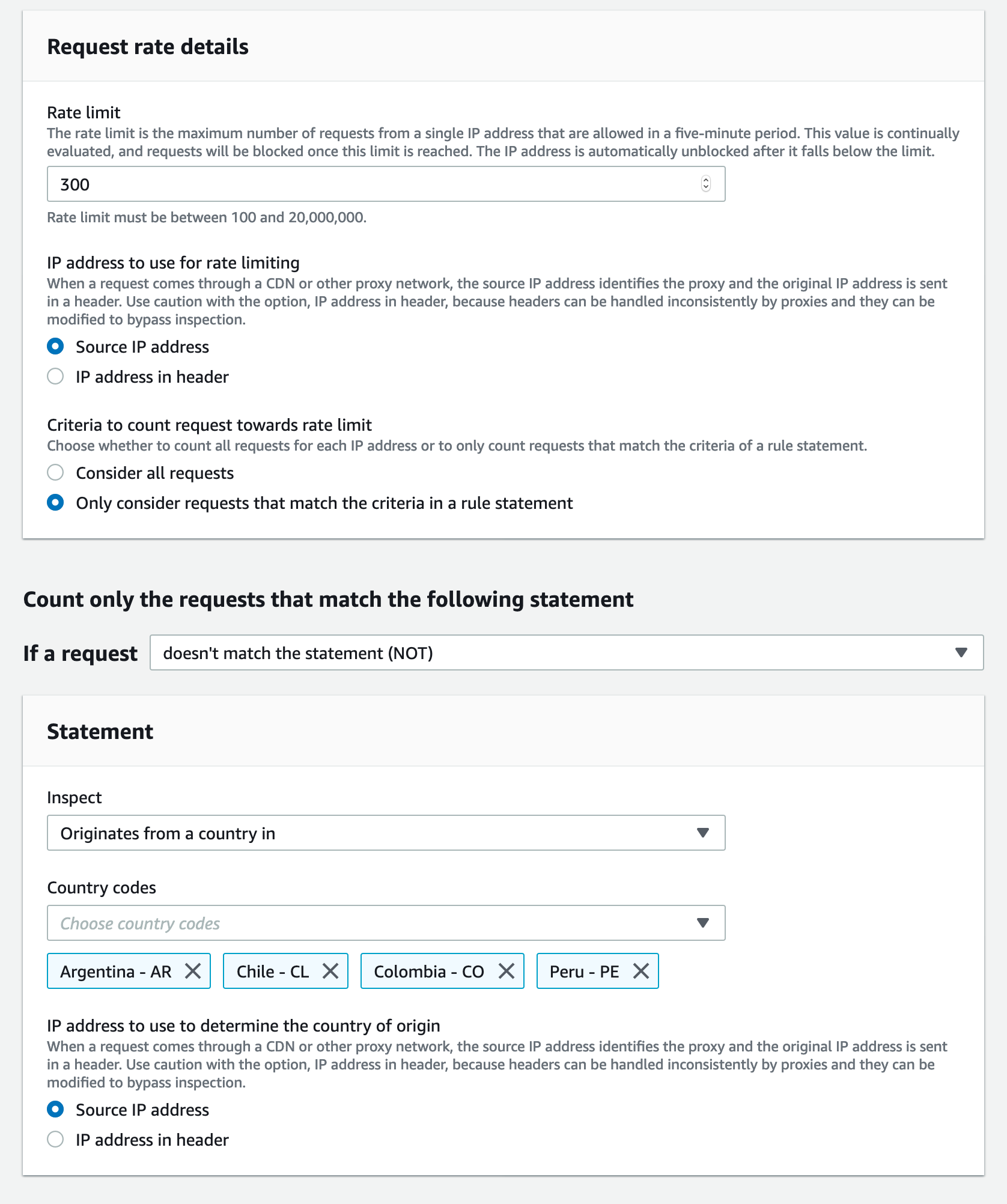 Or limit it specifically in some countries from where attacks are being observed, or do not expect traffic.
Or limit it specifically in some countries from where attacks are being observed, or do not expect traffic.
Protect the account creation process
AWS WAF provides an optional feature to protect the registration form of your applications to prevent malicious bot registrations, or abusing the free tiers or free trials in your application. It’s called AWS WAF Account Creation Protection (ACP)
Protect your customer accounts against takeover
AWS WAF provides an optional feature to protect the login form of your applications to prevent credential stuffing or password spraying attacks. It’s called AWS WAF Account Takeover Protection (ATP)
WAF from our partners
In this phase you should evaluate your application security needs and analyze whether your use case fits AWS WAF capabilities or if you require a third-party solution.
There are multiple solutions available from our partners to protect your cloud applications, such as Imperva , F5 and Fortinet .
If you decide to implement a third-party WAF, you can choose to implement a Firewall as a Service (FWaaS - SaaS) in which case you should direct the domains to your WAF solution so that traffic arrives filtered to AWS, or deploying a Virtual Private Cloud (VPC) for ingress with an Application Load Balanced and a Scaling Group with Virtual Appliances of the WAF in multiple Availability Zones and make the traffic pass through this VPC before reaching its applications.