Integration with SIEM/SOAR
Integration with Security Information and Event Management (SIEM)
In environments with hybrid infrastructure a SIEM is often used to centralize events (on-prem / multi-cloud), to have a central repository where events are analyzed and rules are configured to detect incidents based on different use cases required to achieve business objectives.
Most of the SIEM solutions in the market have the ability to collect data from AWS (AWS Cloudtrail, AWS Security Hub findings, etc.), here’s a list of some of the vendors that can collect AWS logs:
- Splunk
- IBM Security QRadar
- Sumo Logic
- Securonix
- Exabeam
- Rapid7
- Logrhythm
- Microfocus (arcsight)
- Gurucul
- Microsoft Azure Sentinel
- Etc.
Is AWS Security Hub a SIEM ?
No. SIEM Solutions aggregate Events (like a firewall accepted message), then correlates to generate Security Findings / Offenses. AWS Security Hub aggregates Findings (information relevant for the security team to take an action).
Splunk:
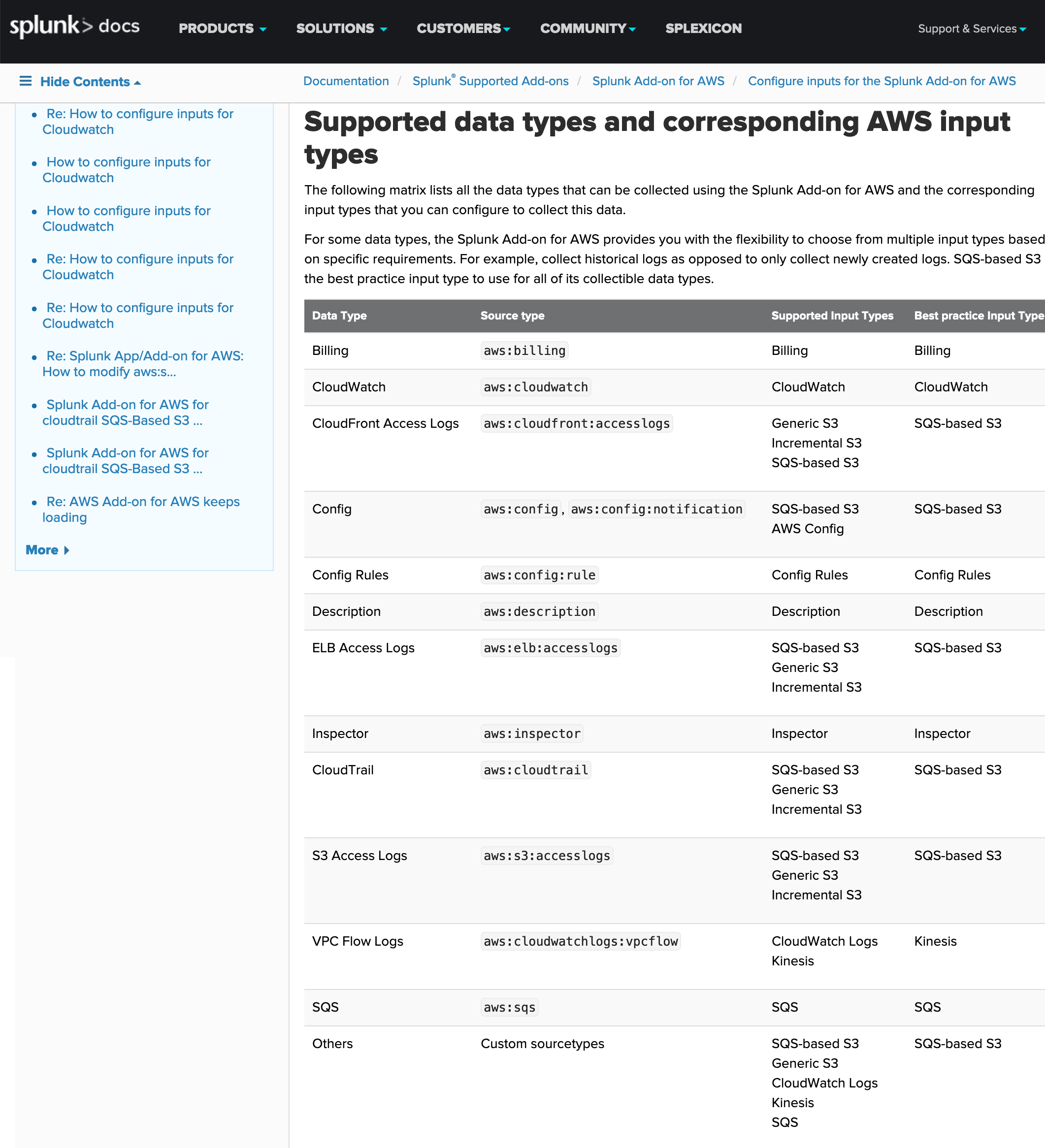
Splunk has the ability to integrate cloud logs, as can be seen in the following image of the documentation:
Add-on en SplunkBase:
https://splunkbase.splunk.com/app/1876/
[Link to add-on documentation ]
QuickStart Splunk Enterprise on AWS
QuickStart for splunk deployment in AWS https://aws.amazon.com/quickstart/architecture/splunk-enterprise/
AWS Marketplace
Splunk is available at AWS Marketplace https://aws.amazon.com/marketplace/pp/B00PUXWXNE
IBM Security QRadar:
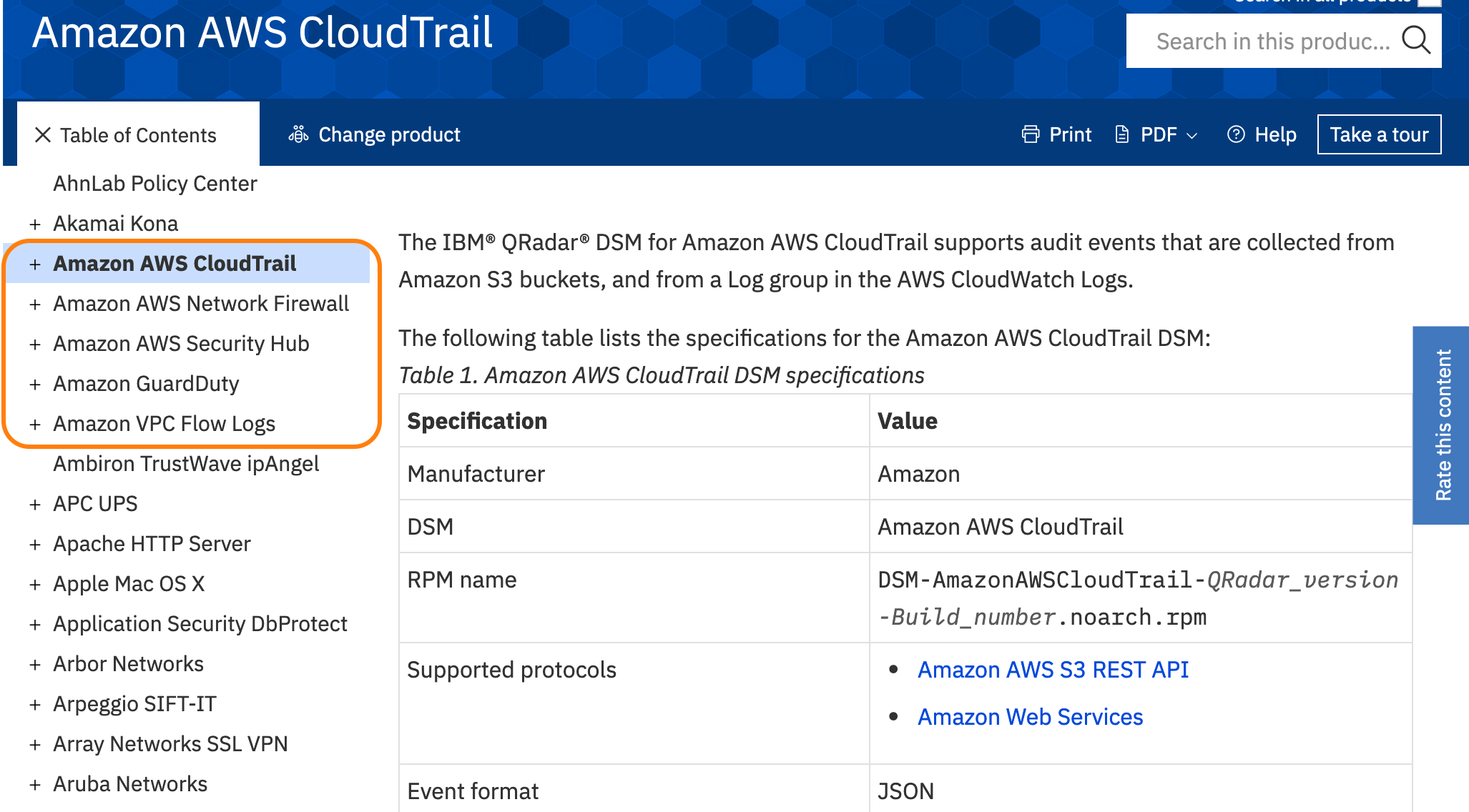
QRadar has the ability to integrate cloud logs, as can be seen in the following image of the documentation:
Extensions in X-Force App Exchange:
AWS Marketplace
QRadar is available at the AWS Marketplace in multiple modalities :
SIEM on Amazon OpenSearch
Alternatively you can deploy a SIEM on an OpenSearch cluster in your AWS Account thru a CloudFormation template available on aws-samples github:
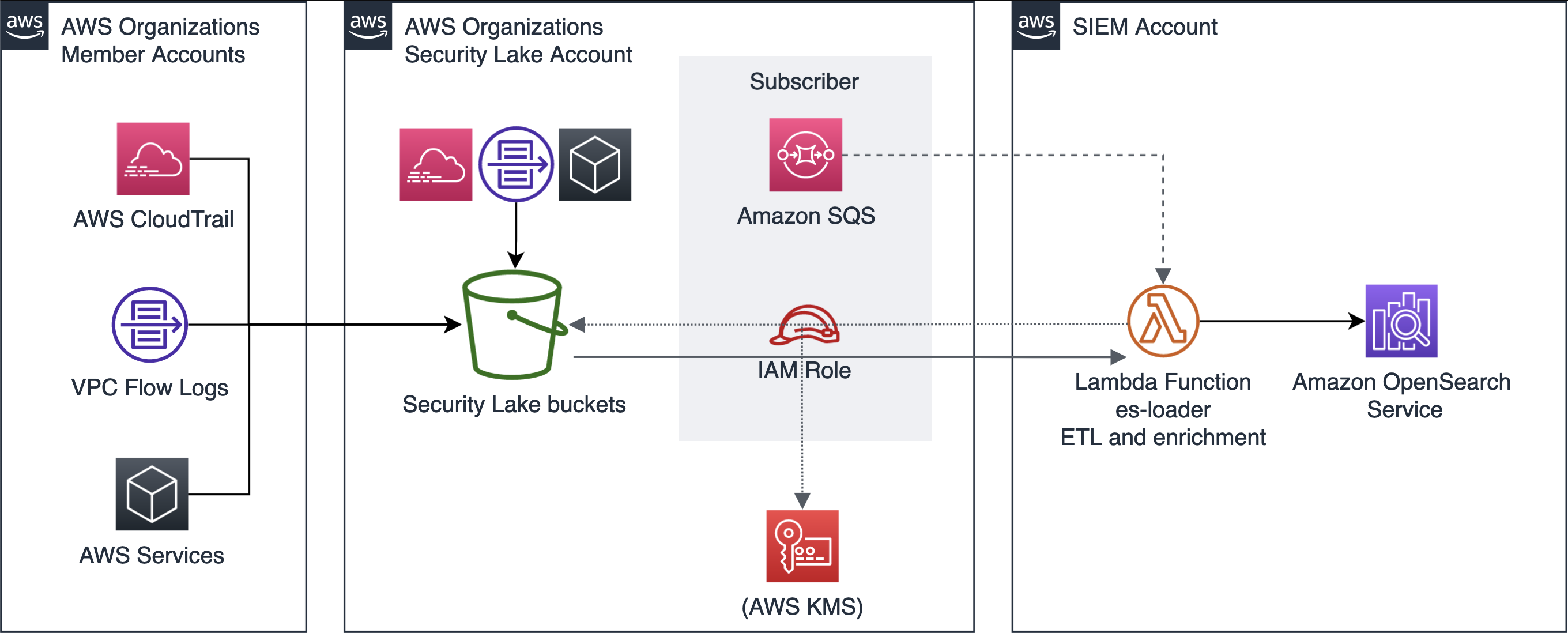 Link to aws-samples in github: https://github.com/aws-samples/siem-on-amazon-elasticsearch
Link to aws-samples in github: https://github.com/aws-samples/siem-on-amazon-elasticsearch
Integration with Security Orchestration, Automation and Response (SOAR)
In a way similar to SIEM, in customers with hybrid infrastructure, A SOAR solution is frequently used to coordinate and automate the incident response process.
The main SOAR solutions have integration with AWS Security Hub, and with AWS in general to take actions.
Splunk Phantom - Integration with AWS Security hub

Palo Alto Networks: Cortex XSOAR - Integration with AWS Security Hub