Investigate most Amazon GuardDuty findings
Investigate most Amazon GuardDuty Findings
A key task among foundational detective controls is to review most Amazon GuardDuty findings. In other words, not only take action on critical finding, but also evaluate why medium or low priority findings are being generated, to detect early attempts of compromise, and quickly block the adversary and activate the incident response plan.
For example, when you detect SSH Bruteforce , it indicates that an adversary is trying to access your exposed SSH services, even if the adversary was unable to enter yet, it is an alarm sign that should direct us towards evaluating alternatives to close that attack vector, such as the use of AWS Systems Manager Fleet Manager
Review reconnaissance findings to identify attacks as they attempt to expand laterally, pentesting tools, and anomalies.
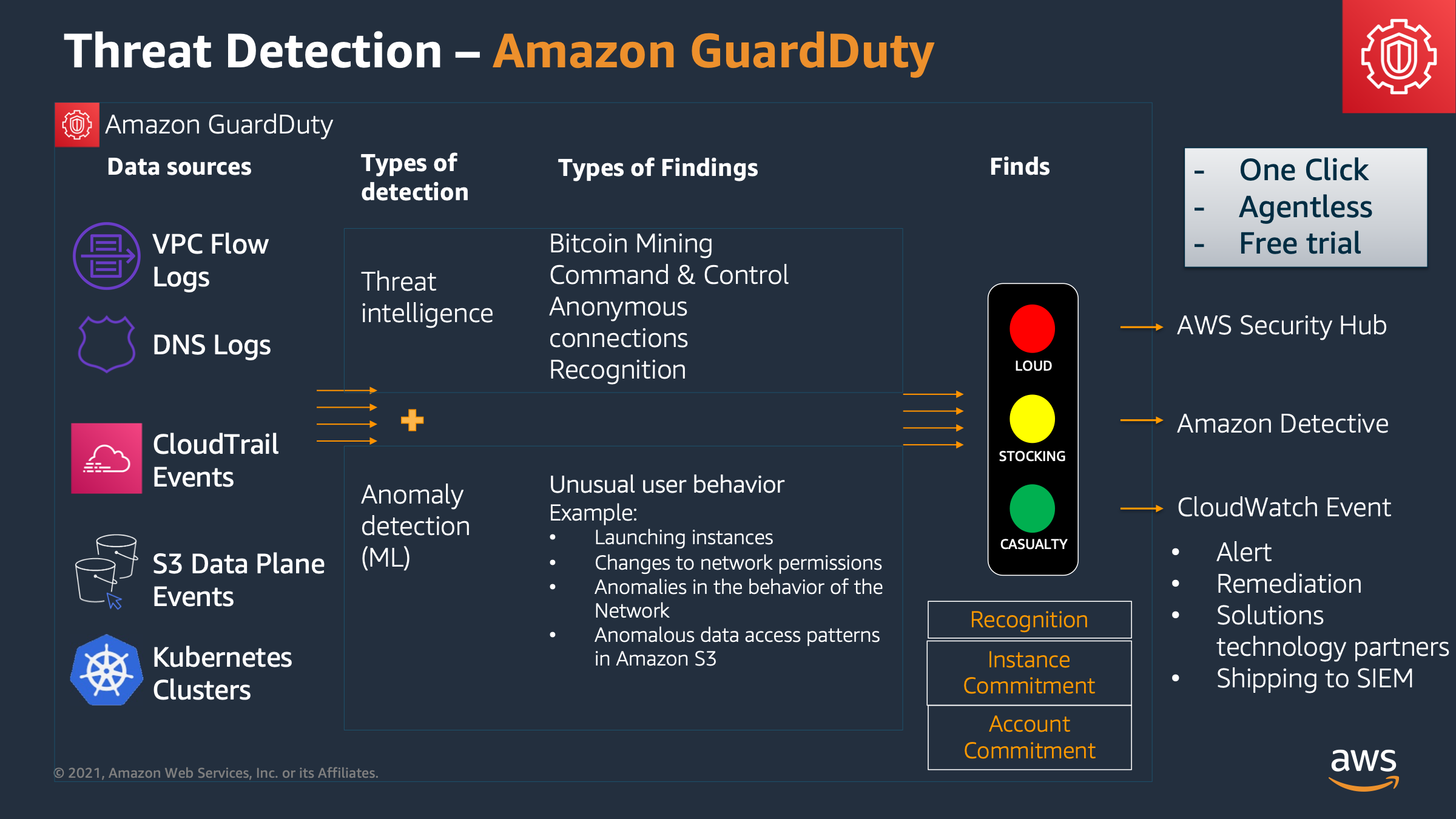
GuardDuty S3 Protection & Kubernetes
GuardDuty has added two optional set of controls for customers using Amazon S3 or Kubernetes clusters. If you are using these services I strongly recommend to enable Amazon GuardDuty features to improve the visibility on these services.
GuardDuty S3 Protection Findings
 See documentation at: https://docs.aws.amazon.com/guardduty/latest/ug/guardduty_finding-types-s3.html
See documentation at: https://docs.aws.amazon.com/guardduty/latest/ug/guardduty_finding-types-s3.html
See also: Enable Amazon GuardDuty for threat detection and respond based on its findings
Workshops
- https://hands-on-guardduty.awssecworkshops.com/
- https://scaling-threat-detection.awssecworkshops.com/
Pricing
https://aws.amazon.com/guardduty/pricing
The service has a 30-day trial period (free trial)
You can verify current usage and estimate future usage of this service.