Create your isolated environment for PCI-DSS Compliance
Compliance @ AWS Cloud
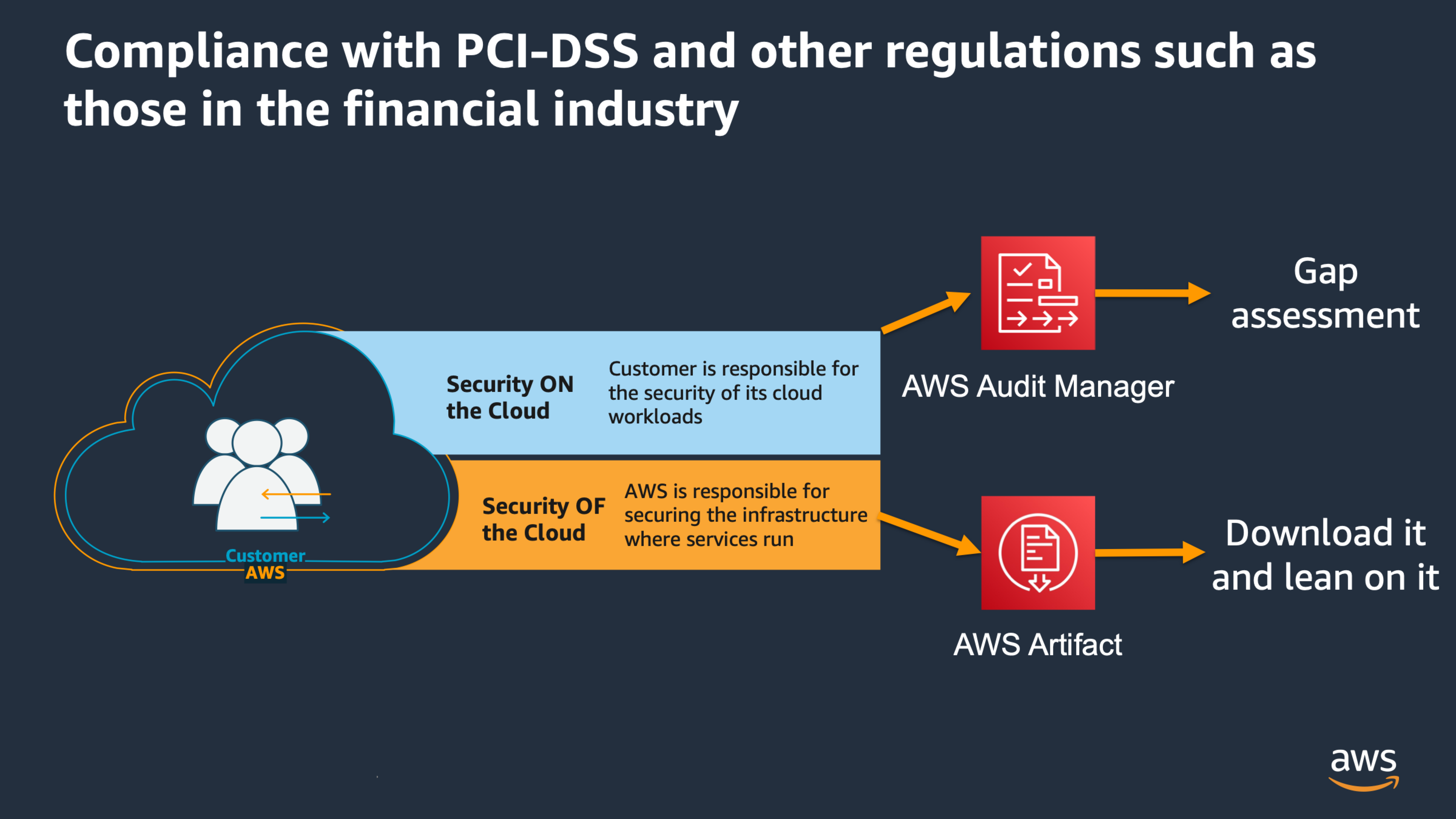
As mentioned in Create your reports for compliance , there is a shared responsibility also for compliance. While AWS will provide you with the compliance documents you need to prove that the AWS Infrastructure is compliant to multiple regulations, and you have to prove to your auditors that the workloads that you have deployed on AWS are also compliant with that regulation (a GAP Assessment) and you can leverage AWS Audit Manager to automate collection of evidence for multiple regulations
For PCI Compliance in particular, the most important recommendation is to segregate the PCI environment from the rest of the workloads
You can optionally leverage the service AWS Audit Manager to automate collection of evidence for multiple regulations (See more on Supported Frameworks ), and composing the report based on information that the service can gather from AWS CloudTrail, AWS Security Hub and AWS License Manager, along with the evidence you manually attach.
PCI Compliance
Organizations that need to meet the Payment Card Industry (PCI) Data Security Standard (DSS) have some additional requirements to comply with in order to deploy workloads that manage credit card information.
To demonstrate to auditors “Security OF the cloud” compliance that is, AWS’ responsibility within the shared responsibility model, you can use the PCI-DSS report in AWS Artifact .
You can also deploy a PCI-DSS compliant standarized architecture using AWS Quickstart .
Detailed information on compliance for each requirement can be found in the following AWS Whitepaper Payment Card Industry Data Security Standard (PCI DSS) 3.2.1 on AWS .
See Services in scope for a detailed list of the services that were certified by different standards and compliance programs including PCI-DSS. For loads requiring PCI-DSS compliance, your services should be limited to those that are validated. Fortunately for PCI-DSS they are the vast majority.
To achieve compliance for our cloud loads, we recommend that you perform the following tasks, in addition to those recommended by your audit team:
-
Limit the scope: the more you can limit your certification scope by isolating the parts that have credit card data flows on different accounts, the more you reduce the burden for compliance, risk, and impact area in case of compromised credentials and is good practice in many aspects. For additional information see Architecting for PCI DSS Scoping and Segmentation on AWS .
-
Enable AWS Security Hub with the PCI-DSS security standard check (CIS AWS Foundation and AWS Foundational best practices standards are also recommended to strengthen your security posture although you may find recommendations that are not required for PCI).
-
Use abstract / encapsulated services to reduce the scope of the PCI-DSS review and lean more on the certifications achieved by AWS.
-
Encrypt any data related to PCI workloads. AWS KMS allows you to have your own encryption keys that you can manage yourself (rotate, disable, or remove), which is often required by auditors. AWS CloudHSM also enables you to meet these requirements.
-
Enable Amazon GuardDuty and review findings (Intrusion Detection).
-
Enable Amazon GuardDuty S3 Protection (to detect potential data leaks).
-
Enable Amazon Macie to detect potential misconfigured access policies, and ensure your credit card data is encrypted with private keys (AWS KMS).
-
Use Amazon Macie to run data discovery and classification jobs, to demonstrate to the auditor that no sensitive data is stored and to ensure access control with to the minimum required privileges (least privilege).
-
Use Web Application Firewalls such as AWS WAF in applications (thus removing the application pentesting requirement for Internet-exposed applications). Other secure development requirements are still needed, such as annual training.
-
If you were providing services other than web services protected by WAF (80/443), it is recommended to deploy a Network Intrusion Prevention System, for this you can use AWS Network Firewall, or there are numerous solutions in the AWS Marketplace to do so.
There is also a specific website with FAQs related to PCI-DSS compliance and other resources.
Among what AWS Professional services (ProServe) provides there is the Security Assurance Services to align your cloud loads with PCI-DSS requirements. The services are provided by QSAs also certified in AWS security, so they can assist you to be ready for a final review by your auditor. Contact your AWS Account Manager if you want to know how to employ their services.
It is always recommended to consult with a PCI expert on how to secure your cloud loads for PCI-DSS compliance.