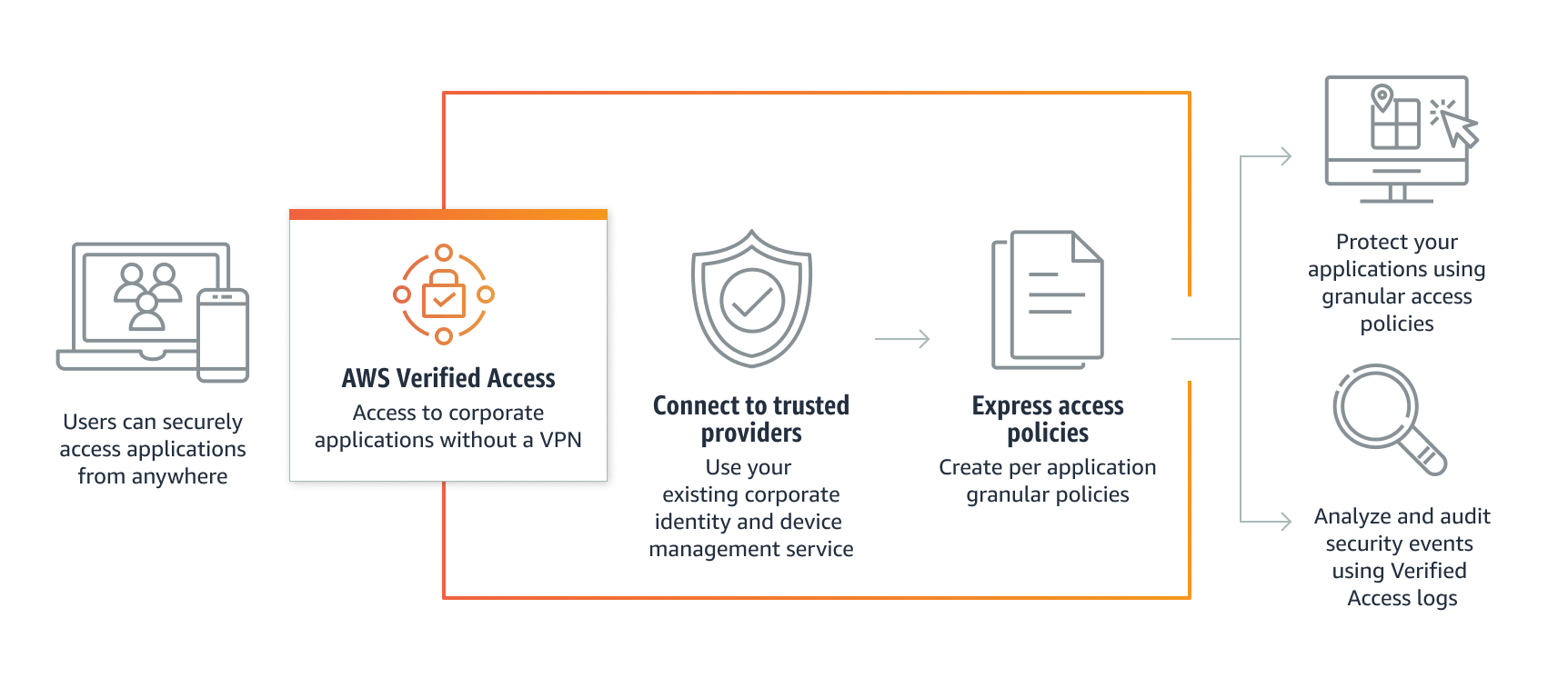
Zero Trust Access: Risk-Based Access Control
Implement Risk based access controls for VPN-less access to internal applications
To reduce friction and improve the security of your applications use context as an additional factor for authentication. You can use information such as the network source, if the anti-malware is running/updated, if using an approved OS, or looking for particular configurations in your workstations to identify signals that indicate there’s an anomaly and additional verifications should be activated, such as Multi-Factor Authentication.
AWS Verified Access can help:
- Authenticating your applications with your identity provider (such as Okta or AzureAD)
- Gathering context information from 3rd party trust providers such as CrowdStrike and JAMF
- Combining the information from the identity and trust providers with the requested resource in policies to define in which conditions to allow access.
AWS Verified Access uses Cedar , an open source language optimized for fast processing and supporting zero trust conditions.