Threat Intelligence
Threat Intelligence Team
Form a Threat Intelligence team that works studying local and global security news, threat actors, tactics, indicators of compromise (IoC) and feeds that intelligence into your security services and solutions.
Adding IPs to the GuardDuty threat list
The threat detection service Amazon GuardDuty natively uses Amazon’s own intelligence sources, third-party sources such as CrowdStrike and Proofpoint, and some OpenSource sources (such as the list of exit nodes of the TOR anonymization network)
However, if you detect malicious IPs attacking your on-prem, you could add them to GuardDuty’s threat lists so that the service alerts against access from those IPs.
Another frequent use case is when they have contracted a threat intelligence service (such as Talos, X-Force, FireEye, etc) and would like to add their indicators of compromise (malicious IPs) they can do so on the following screen:
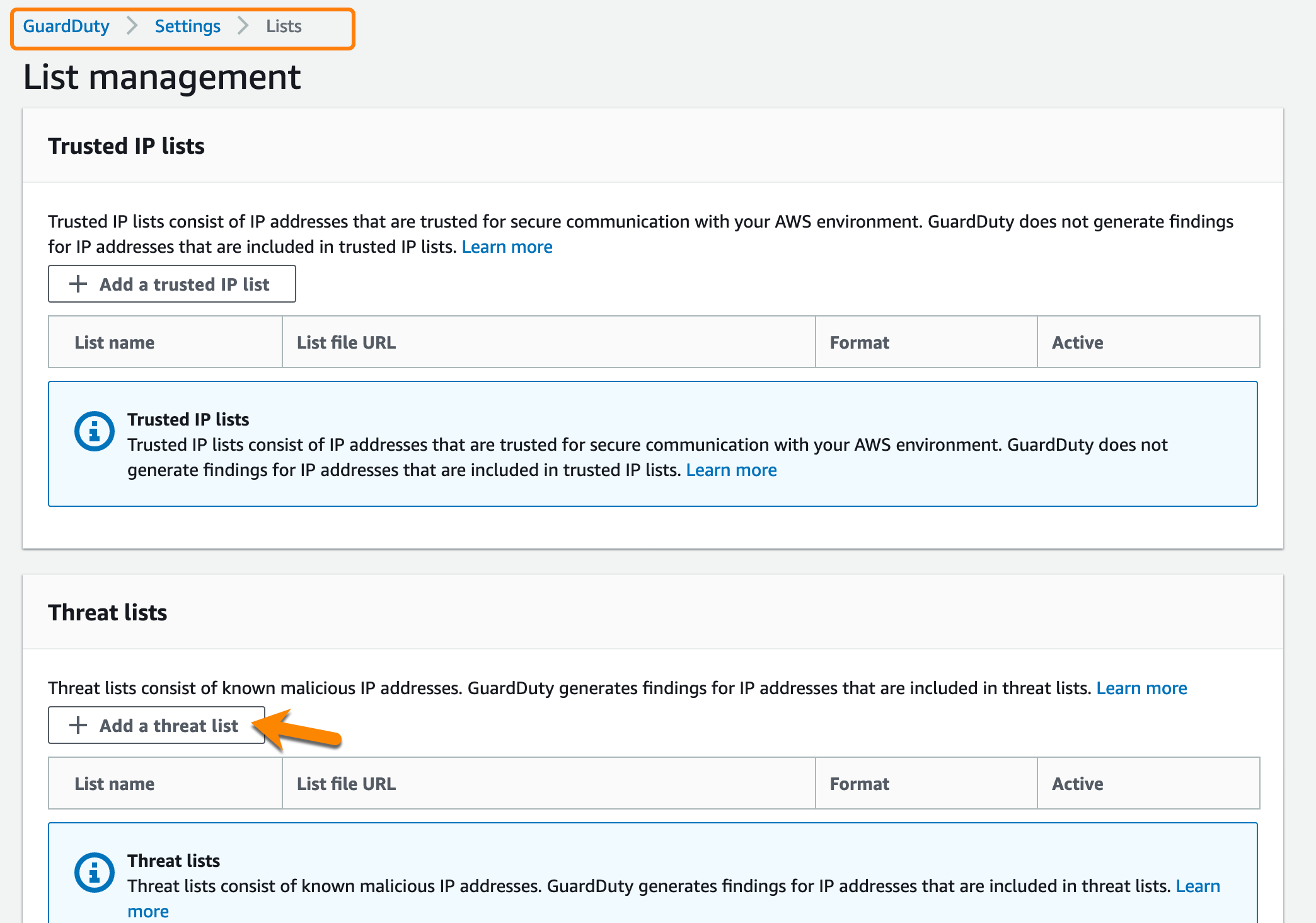
Supported formats:
- Plaintext (TXT)
- Structured Threat Information Expression (STIX)
- Open Threat Exchange (OTX - CSV)
- FireEye iSight threat intelligence (CSV)
- Proofpoint ET Intelligence Feed (CSV)
- AlienVault Reputation Feed
AWS Web Application Firewall
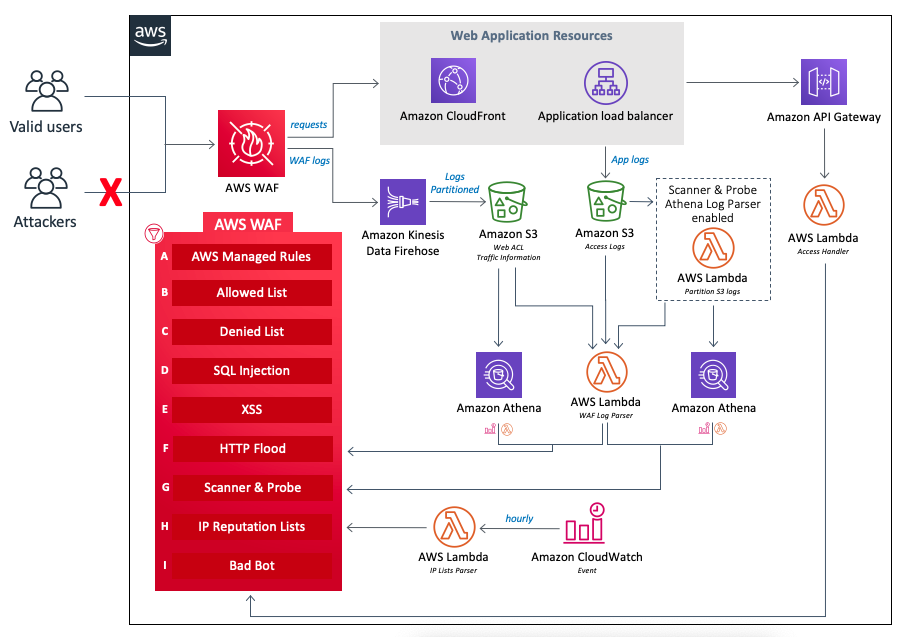
AWS WAF natively has IP reputation lists among its Managed Rules (Amazon IP Reputation, and Anonymous IP List), which are particularly useful for reducing the number of attacks from malicious botnets.
You can enrich this list of IPs with rules managed by our partners in the AWS Marketplace, such as F5, GeoGuard, Imperva.
WAF Security Automations
WAF Security Automations is a solution that implements a number of additional protections for WAF, including intelligence feeds from SpamHaus, TORproject, and EmergingThreats.
HoneyPots, decoys & deception
If you have a trained team dedicated to threat intelligence and would like to get your own signals, implementing HoneyPots if it’s properly done, can provide fresh data to the threat intelligence team
The following blogpost can assist you with setting up honeypots in AWS: https://aws.amazon.com/blogs/security/how-to-detect-suspicious-activity-in-your-aws-account-by-using-private-decoy-resources/
Guidance for assessments
- Are you implementing mechanisms to add malicious IP Address to GuardDuty threat list? (for example, notices from a local CIRT, or if an unauthorized outside party attempts to access your on-prem environment by a remote IP address)
- Are you integrating 3rd party threat intelligence feeds ?
- Do you have a threat intelligence team ?
- Are you leveraging honeypots to learn about your adversaries ?