IAM Data Perimeters: Conditional Access
As organizations extend their presence in the cloud and try to achieve higher levels of business agility by adopting decentralized approach to cloud operations, they are looking for ways to prevent risks associated with configuration mistakes and unintended access to their data. Data perimeters on AWS is one of the mechanisms that we have seen enterprises successfully use to reduce these risks and improve the security posture of their multi-account cloud environments.
Data perimeter definitions
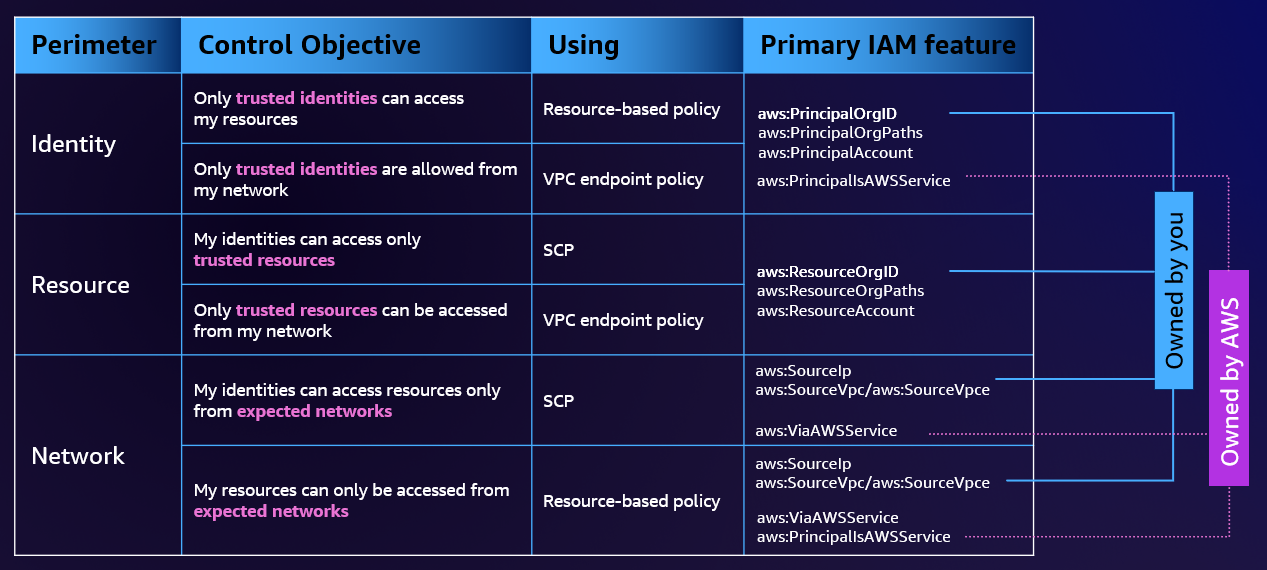
A data perimeter is a set of permissions guardrails that help ensure that only trusted identities are accessing trusted resources from expected networks. Data perimeter guardrails are meant to serve as always-on boundaries to help protect customer data across a broad set of AWS accounts and resources. These organization-wide guardrails do not replace fine-grained access controls. Instead, they help advance through the least privilege journey in a more agile manner by enforcing security invariants.
Trusted identities: Principals (IAM roles or users) within your AWS accounts, or AWS services acting on your behalf. Trusted resources: Resources owned by your AWS accounts or by AWS services acting on your behalf. Expected networks: Your on-premises data centers and virtual private clouds (VPCs), or networks of AWS services acting on your behalf.
Data perimeter objectives
Data perimeter journey
Data perimeter controls should be treated as any other security control within the information security and risk management program. This means that you should perform a threat analysis to identify potential risks within your cloud environment, and then, based on your own risk acceptance criteria, select and implement appropriate data perimeter controls. To better inform the iterative risk-based approach to data perimeter controls implementation, you need to understand what security risks and threat vectors are addressed by the data perimeter framework as well as your security priorities.
You can learn more about security risks addressed by each perimeter type by reading the data perimeter blog series, which you can find on the Data perimeters on AWS page along with other resources to help guide the implementation.
Data Perimeters Landing page
https://aws.amazon.com/identity/data-perimeters-on-aws
Workshop
Risk Mitigation
- Configuration errors in IAM or resource-based policies may leave resources exposed to unintended access.
- Unintended data disclosure through non-corporate or stolen credentials.
Guidance for assessments
- Are you leveraging Data perimeters to secure your critical applications?
- Have you implemented resource control policies (RCP) to prevent access to your resources from outside your organization?
- Are you controlling with IAM condition keys that access to critical applications and resources (such as S3 buckets) is ONLY allowed from where it is expected?
Video
AWS Documentation
Pricing
AWS IAM service is free and configuration of service control policies (SCPs) or resource control policies (RCPs) have no additional cost