Custom Threat Detection capabilities - SIEM / Security Lake
Why custom threat detection capabilities ?
While Amazon GuardDuty has many threat detection capability, it doesn’t offer the possibility to create detections for custom use cases. For custom threat detection you need to:
- Identify your use cases
- Identify the log sources with the data required for your use cases
- Centralize events / log sources
- Create correlation rules to detect offenses with categorization
- Define alerting based on categorization
Building a Security Lake
To centralize diverse event logs in a multi-account environment to a centralized data lake with the data normalized to the Open CyberSecurity Schema Framework you can leverage Amazon Security Lake a service that scales to petabytes, and simplifies integration with 3rd party enterprise security solutions that send data to the lake such as CrowdStrike, Palo Alto, Tanium, and Okta, and solutions that can query the lake or receive the normalized events such as Security Information and Event Management (SIEM) solutions (that work as subscribers), business intelligence tools and you can query the whole lake with Amazon Athena . With a Security Lake you can maintain a smaller period of time in the visualization tools and still keep the record of all logs in a searchable format for years.
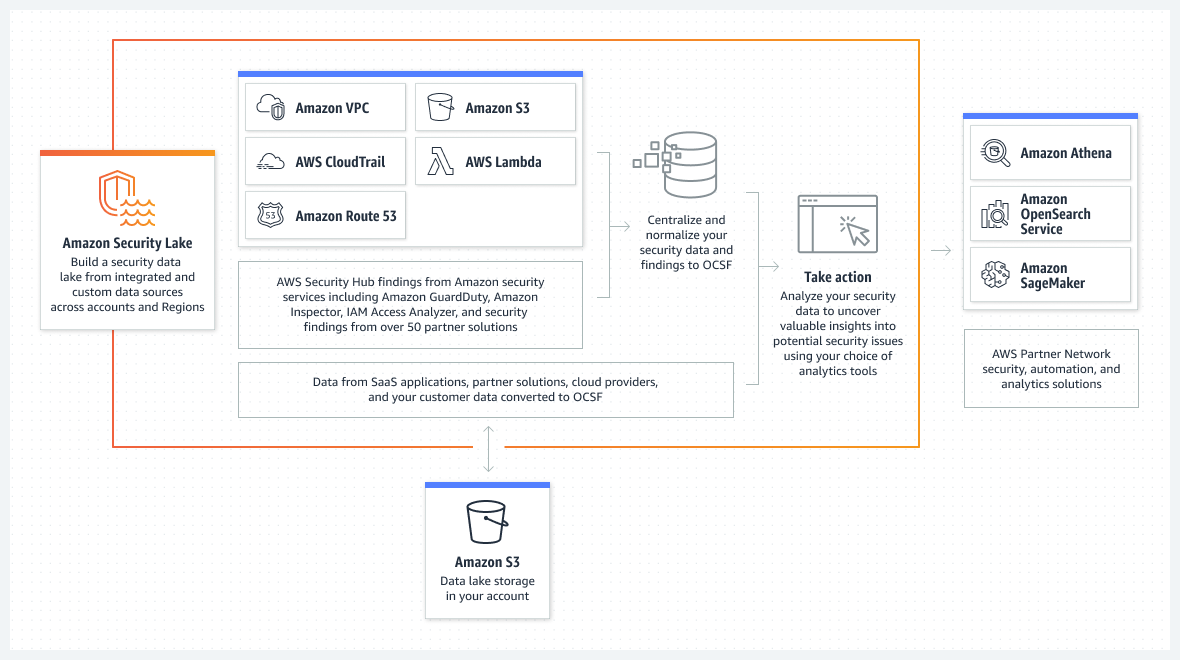
Integration with Security Information and Event Management (SIEM)
In environments with hybrid infrastructure a SIEM is often used to centralize events (on-prem / multi-cloud), to have a central repository where events are analyzed and rules are configured to detect incidents based on different use cases required to achieve business objectives.
Most of the SIEM solutions in the market have the ability to collect data from AWS (AWS Cloudtrail, AWS Security Hub findings, etc.), here’s a list of some of the vendors that can collect AWS logs:
- Splunk
- IBM Security QRadar
- Sumo Logic
- Securonix
- Exabeam
- Rapid7
- Logrhythm
- Microfocus (arcsight)
- Gurucul
- Microsoft Azure Sentinel
- Etc.
Is AWS Security Hub a SIEM ?
No. SIEM Solutions aggregate Events (like a firewall accepted message), then correlates to generate Security Findings / Offenses. AWS Security Hub aggregates Findings (information relevant for the security team to take an action).
SIEM on Amazon OpenSearch
You can deploy a SIEM on an OpenSearch cluster in your AWS Account through a CloudFormation template available on aws-samples github:
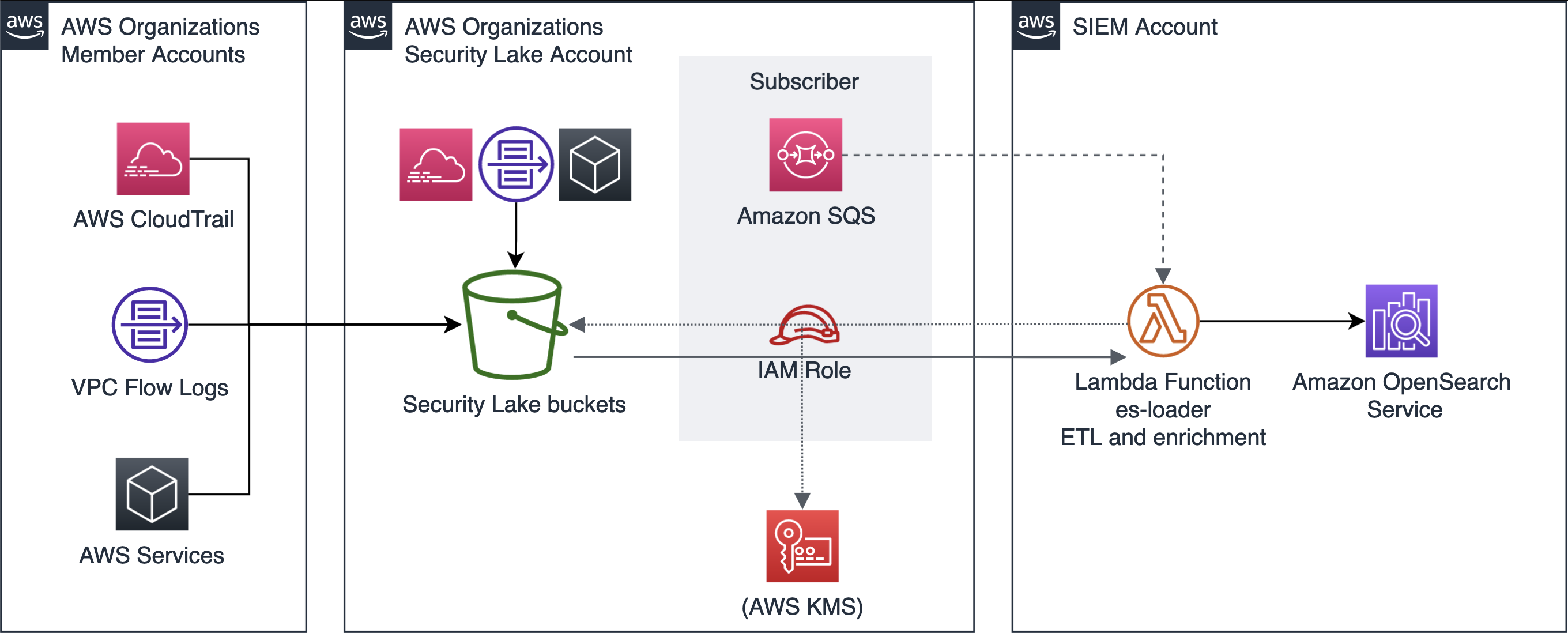 Link to aws-samples in github: https://github.com/aws-samples/siem-on-amazon-opensearch-service
OpenSearch provides 2200 out-of-the-box open-source Sigma security rules.
Link to aws-samples in github: https://github.com/aws-samples/siem-on-amazon-opensearch-service
OpenSearch provides 2200 out-of-the-box open-source Sigma security rules.
Splunk:
Splunk has the ability to integrate cloud logs, as can be seen in the following image of the documentation:
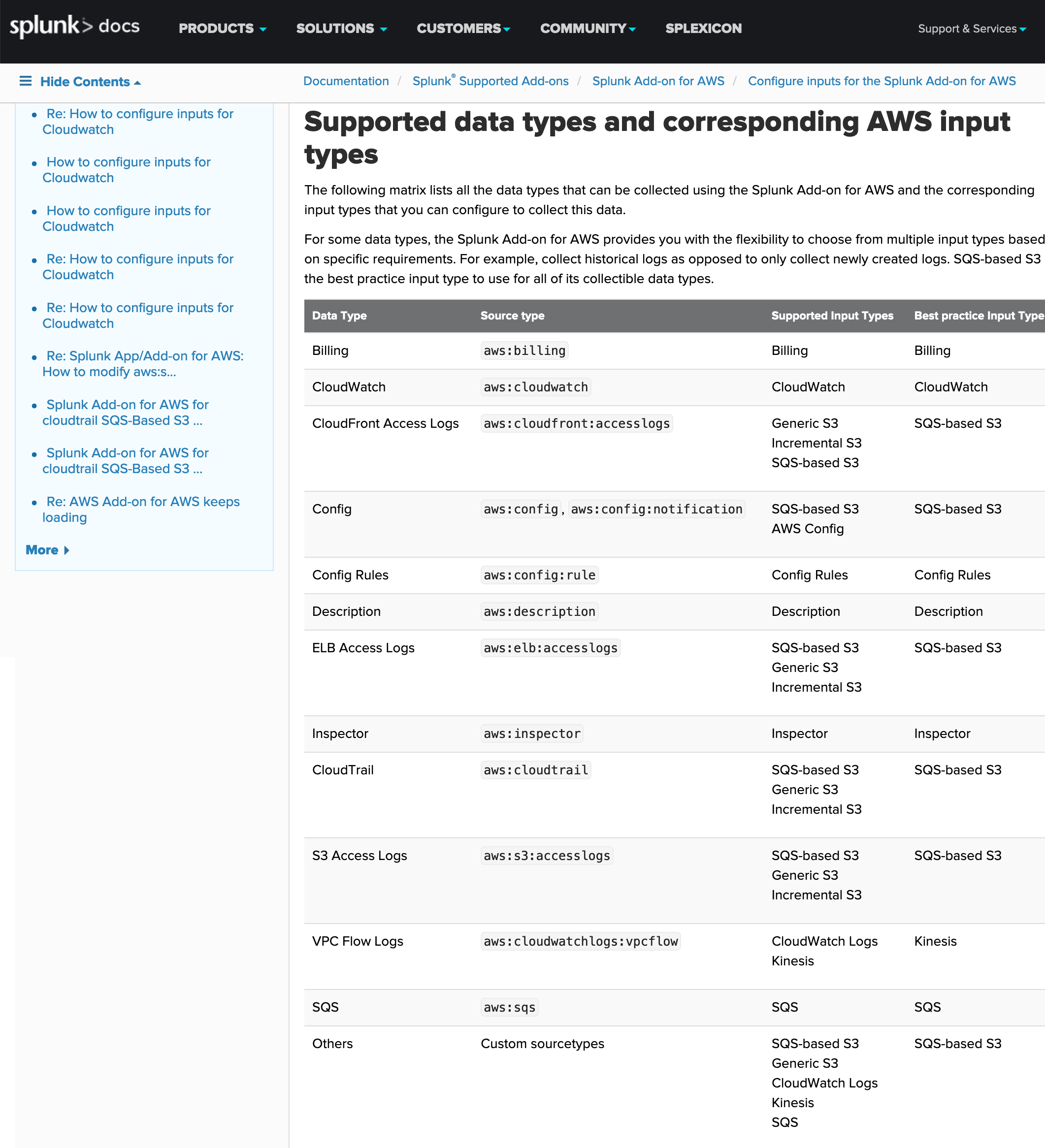
Add-on en SplunkBase:
https://splunkbase.splunk.com/app/1876/
[Link to add-on documentation ]
QuickStart Splunk Enterprise on AWS
QuickStart for splunk deployment in AWS https://aws.amazon.com/quickstart/architecture/splunk-enterprise/
AWS Marketplace
Splunk is available at AWS Marketplace https://aws.amazon.com/marketplace/pp/B00PUXWXNE
IBM Security QRadar:
QRadar has the ability to integrate cloud logs, as can be seen in the following image of the documentation:
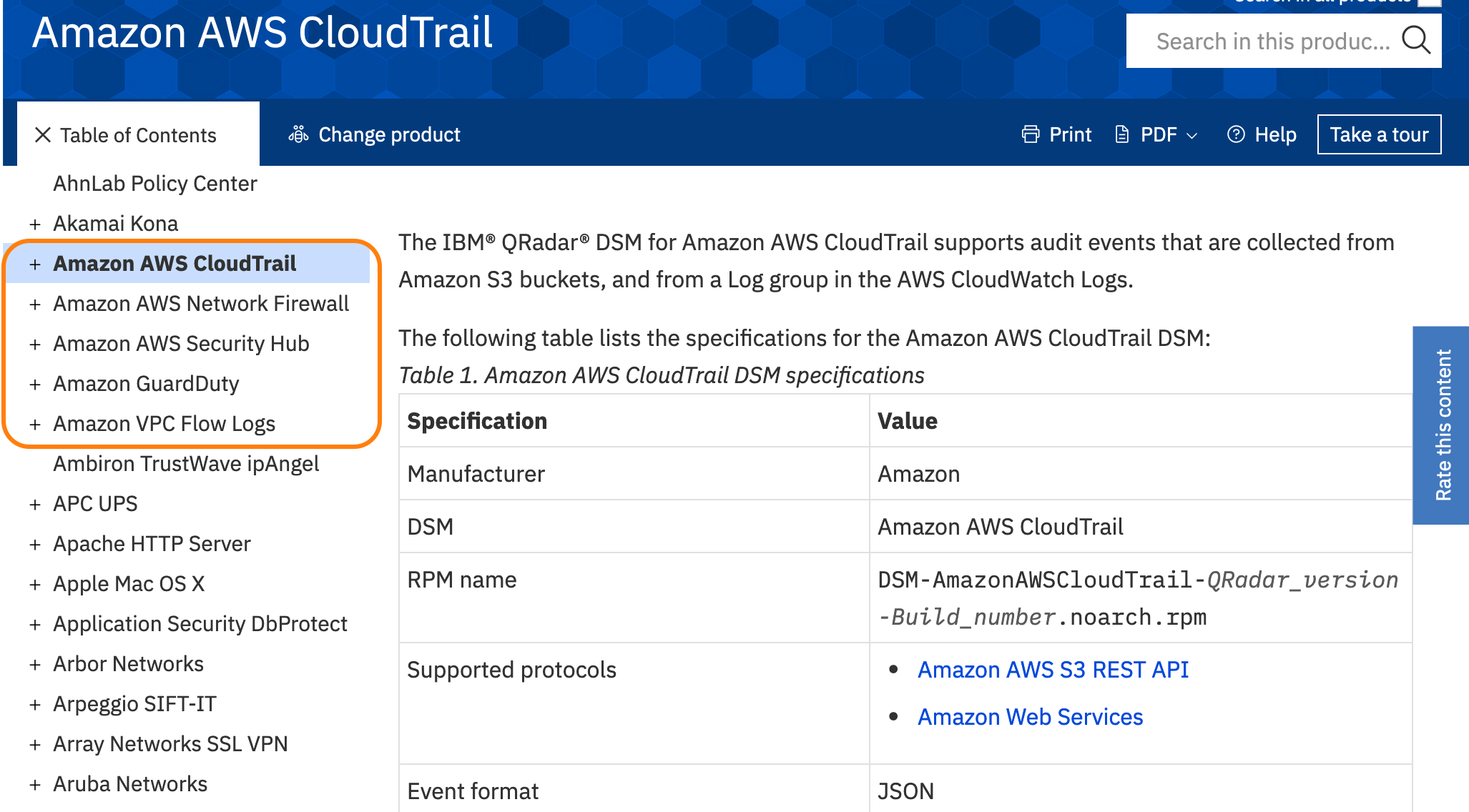
Extensions in X-Force App Exchange:
AWS Marketplace
QRadar is available at the AWS Marketplace in multiple modalities :
Pricing
https://aws.amazon.com/security-lake/pricing
Offers a free trial for 15 days
https://aws.amazon.com/opensearch-service/pricing
Offers a free tier of 750 hours per month, and 10 GB per month of optional Amazon Elastic Block Store (EBS) storage.