Least Privilege Review: Set up right-size permissions in roles
Set up right-size permissions for your IAM roles
Often when developers create roles they’re unsure about which permissions they need to grant, and in the rush to deploy as fast as possible often they require additional permissions that are not required, which does not align with the principle of least principle. Work to remove the unnecessary permissions on IAM roles to approach as closer as possible to the principle of least principle.
IAM Policy Review
Periodic review of your IAM roles is recommended to ensure that they grant the minimum privileges required for the function to perform (least privilege)
https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html#grant-least-privilege
Unintended access review
In particular, review asterisks in policies: … “Action”: “service-prefix”: “*” … or … “Resource”: “*” …
Frequently when these broad permits are granted it is due to lack of dedication/effort in the construction of a more specific IAM policy.
IAM Access Analyzer - Unnecessary access
IAM Access Analyzer can detect unused permissions on roles. Configure an analyzer for your organization and reduce access that is not being used.
IAM Access Analyzer - Policy generation
IAM Access Analyzer has a policy generation capability based on user activity (as reflected on AWS Cloudtrail). Use this functionality to refine policies with excessive permissions, not used in a significant period of time (which will depend on its use case).
https://docs.aws.amazon.com/IAM/latest/UserGuide/access-analyzer-policy-generation.html
Suggest your developers to configure IAM Access Analyzer policy generation on dev accounts with broader permissions, test the application, generate the policy with the minimum privilege, and then use that policy generated to test in you test environment before moving to production.
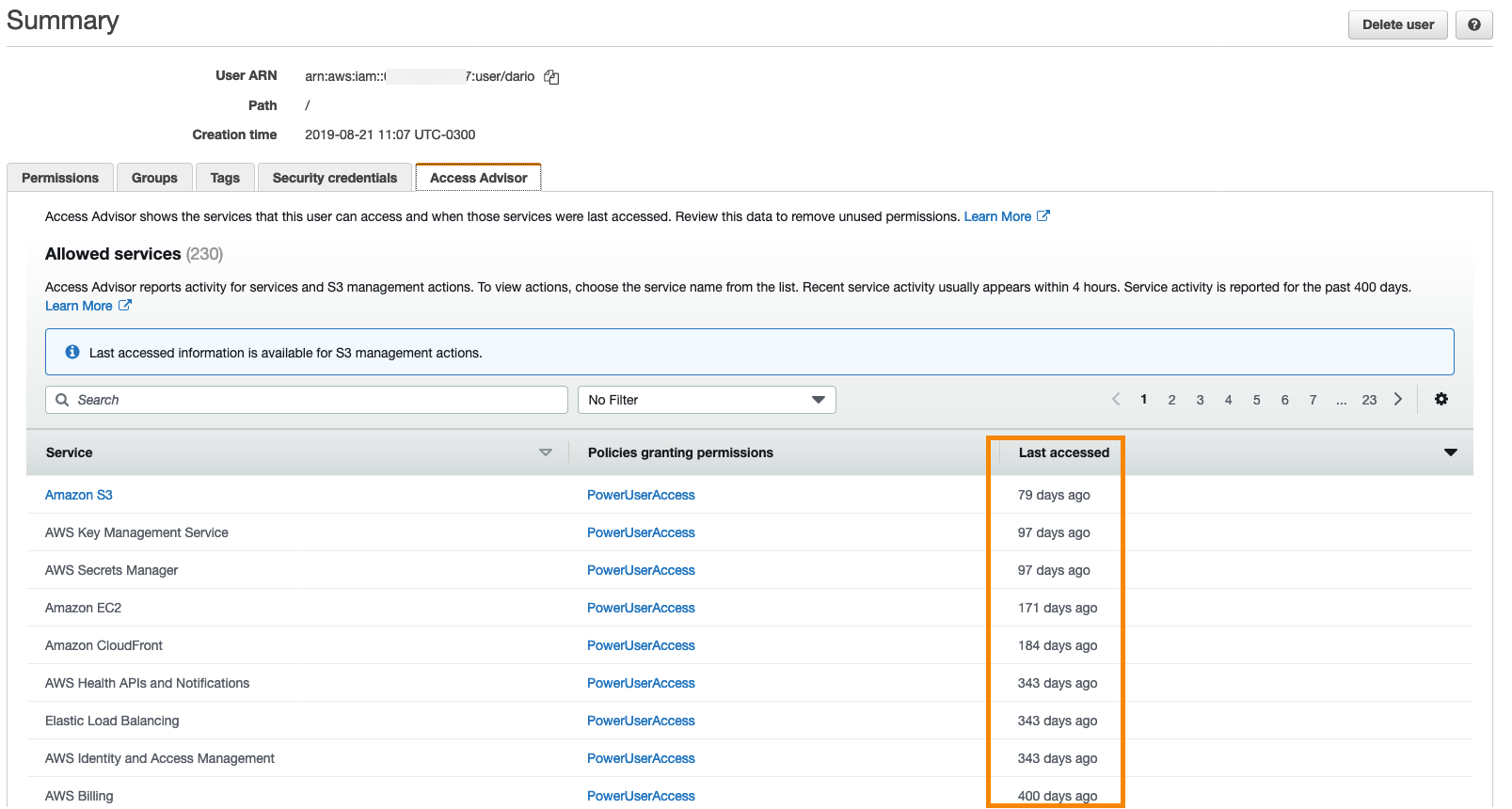
IAM Access Advisor
Use IAM Access Advisor
to identify unused access:
Policy examples:
https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_examples.html
Solutions from our AWS Marketplace Partners:
Alternatively you can review Cloud Infrastructure Entitlement Management (CIEM) solutions such as Ermetic or Sonrai .
Open Source tools
Among the open source tools that can help you discover excessive/unintended permissions there’s CloudSplaining that can show you your policies in a graphic format, and allow you to understand risks associated with over permissive policies.
CloudSplaining GitHub
CloudSplaining Documentation
Well Architected Framework Recommendation Mapping
- SEC03-BP04 Reduce permissions continuously
Blogposts
Strategies for achieving least privilege at scale: [Part 1] [Part 2]