DevSecOps: Security in the Pipeline
The DevSecOps topic is broad, it consists of the development, security and operations team working together in continuous deployment cycles, where functions that each of these teams need are automated, such as compilation/build, provisioning and infrastructure configuration , quality tests, security tests, monitoring, etc.
The particular recommendation related to this point is that your organization adopt this operation model as way of working with processes (pipelines) of continuous deployment, implementing microservices with low cohesion, and ensuring that as part of this deployment, security is taken into account from the very beginning of a software release, as is shown in the following topics:
Operating systems Hardening in pipeline
If you deploy code on instances, take the following precautions:
- The base instances to be used should be created periodically with updated components to avoid vulnerabilities related to known bugs. For this you can use EC2 Image Builder
- As part of the deployment in EC2 Image Builder you can add the Amazon Inspector agent to periodically perform checks to ensure that there are no operating system or application vulnerabilities in the instance.
- Apply security configurations to strengthen the security posture of the operating system. A good starting point are the Center for Internet Security (CIS) guides. Amazon Inspector can verify alignment with CIS operating system standards to verify that they have been applied.
Perform application security testing as part of the pipeline
They can perform security tests on the Code (Static Application Security Testing), with tools such as Veracode or Fortify and dynamic analysis (DAST) with tools such as Aqua or Acunetix , The key point of these revisions is that it be carried out as part of the application deployment process, and that when any high or critical vulnerability is found, the transition to production is interrupted.
The sooner the vulnerabilities are found, the more convenient it will be for the remediation in the effort, economically, and in time.
It also adds value that the tools verify the open source libraries used and report their vulnerabilities.
AWS has a service called AWS CodePipeline
which enables the orchestration of these continuous deployment processes automatically. Example:
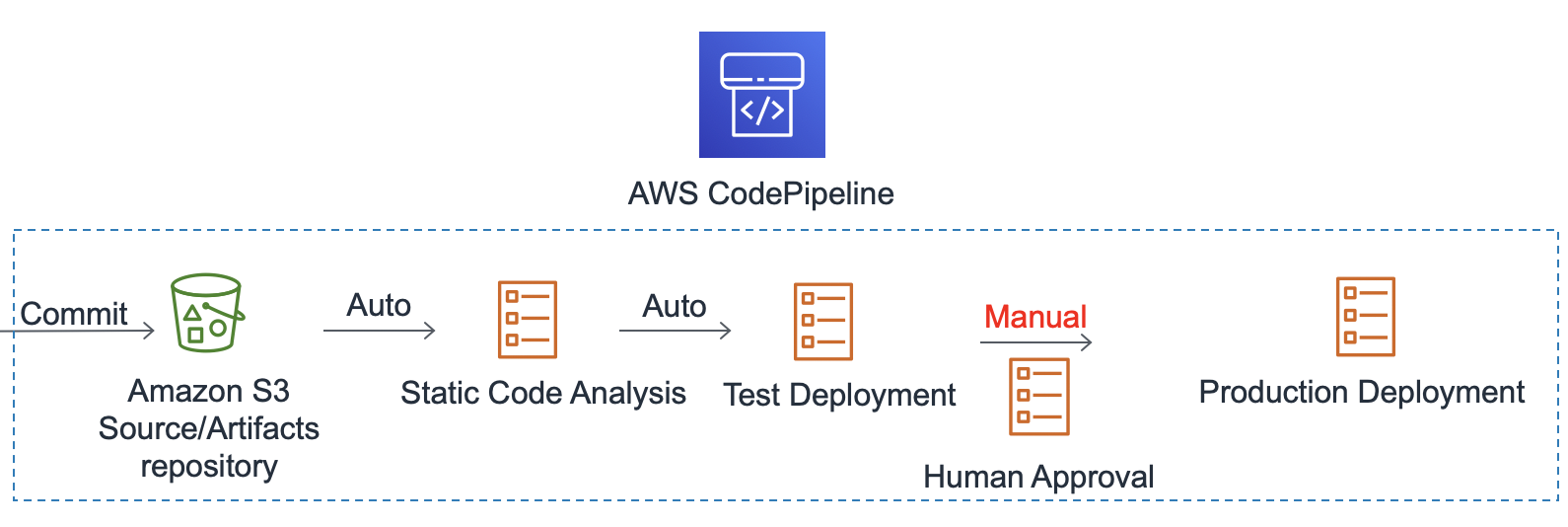
Deployment of security components
If you know of a vulnerability in an application to be deployed that cannot be fixed yet (for example, when there is a dependency on a third party), you can deploy some custom WAF rules as part of the pipeline to protect the application at that point until the error occurs. of code is remedied.
Example: AWS Blog
As an example of the protection infrastructure deployment as part of the continuous deployment (CI/CD) process, it is recommended to review the following blog that shows how to deploy Web ACLs: How to use CI/CD to deploy and configure AWS security services with Terraform
Risk Mitigation
- Many web applications require to be exposed to provide services, therefore vulnerabilities on the applications are accessible by adversaries.
- Most development teams are not experts in security, or do not have time to prioritize secure code practices.
Guidance for assessments
- Are you scanning your application for security vulnerabilties in the pipeline ?
- Are you scanning for secrets / credentials in code in the pipeline? (i.e.: if a developer puts an access key in code, do you detect it?)
- Are you stoping pass to production if critical vulnerabilities are found ?