Create your compliance reports
Compliance @ AWS Cloud
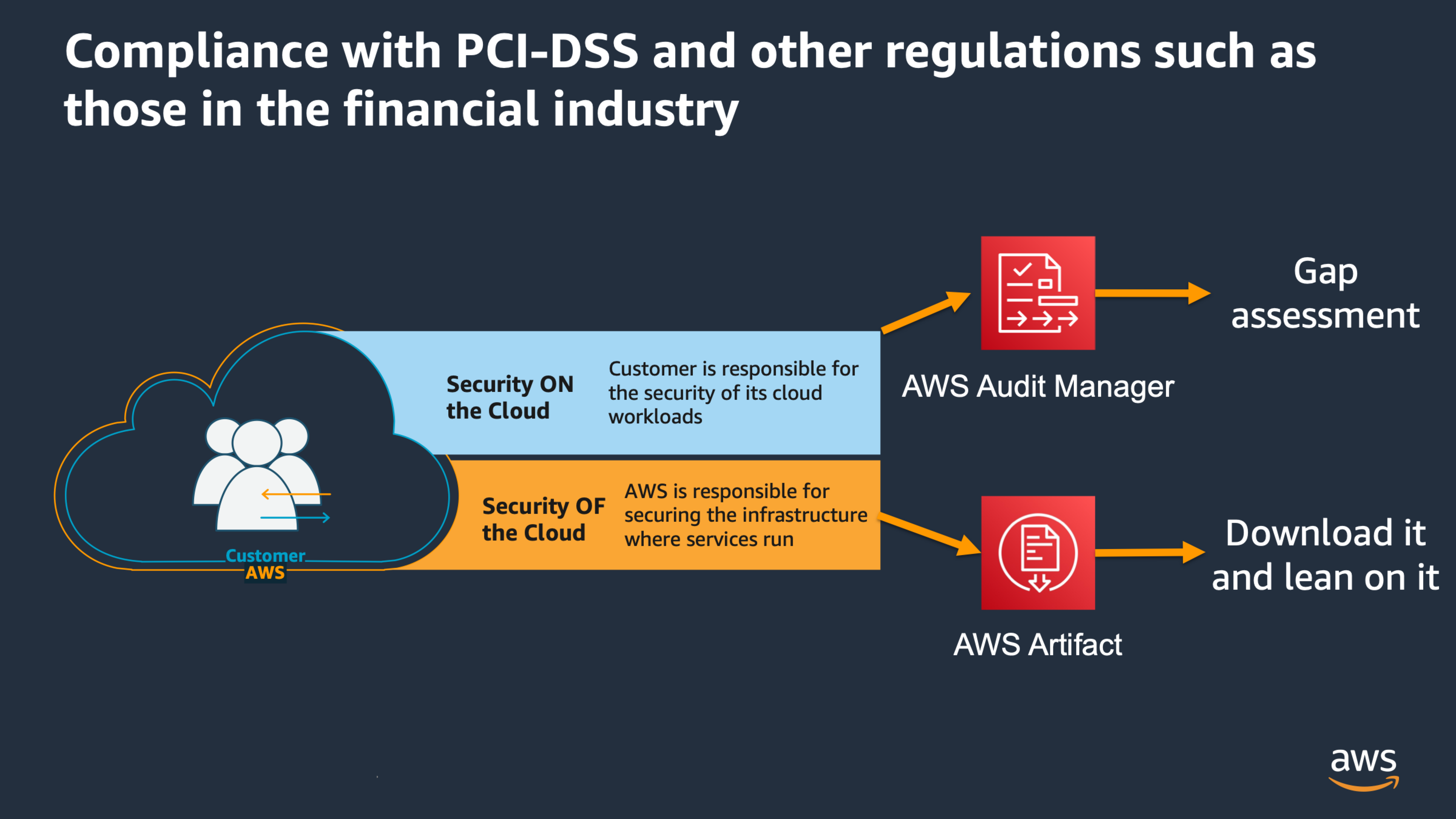
In AWS Cloud there is a shared responsibility also for compliance. While AWS will provide you with the compliance documents you need to prove that the AWS Infrastructure is compliant to multiple regulations, you have to prove to some auditors that the workloads that you have deployed on AWS are also compliant with that regulation (a GAP Assessment)
You can leverage the service AWS Audit Manager to automate collection of evidence for multiple regulations (See more on Supported Frameworks ), and composing the report based on information that the service can gather from AWS CloudTrail, AWS Security Hub and AWS License Manager, along with the evidence you manually attach.
AWS Audit Manager Mindmap
https://www.xmind.net/m/AY2Rgu