Design your secure architecture
Be intentional on architectural decisions
The architecture is an important security control, good architectures reduce attack vectors and impact in case of a breach.
- Avoid the use of exposed SSH/RDP ports, restrict source IP, or better yet, use AWS Systems Manager Fleet Manager that does not require opening inbound ports.
- Limit the lateral expansion of opponents: For example, configure database Security Groups to receive traffic only from instances within the application servers security group (by reference).
- Allow only the minimum required network paths.
- Take advantage of multiple Availability Zones to increase your fault tolerance and disaster resilience.
Review the Well Architected Framework documents to enhance your capacity for secure architectural design.
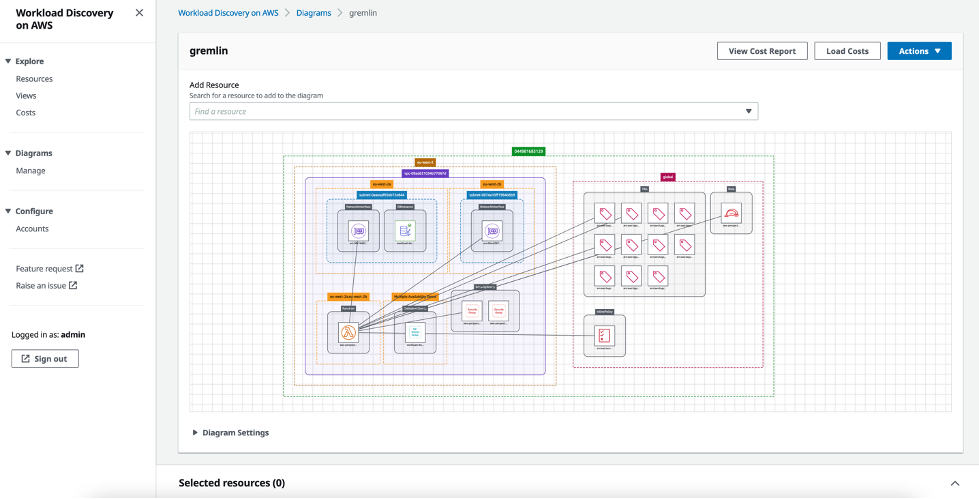
Workload Discovery on AWS Solution
To automatically generate architecture diagrams of your AWS infrastructure, there is a tool called Workload Discovery on AWS that will help you perform architectural reviews, detect hidden resources (Shadow IT), and search by resource name tags, resource name, IP, etc. The visualization it generates is exportable in different formats that allow modifications such as draw.io, CSV, JSON, as well as image (PNG).
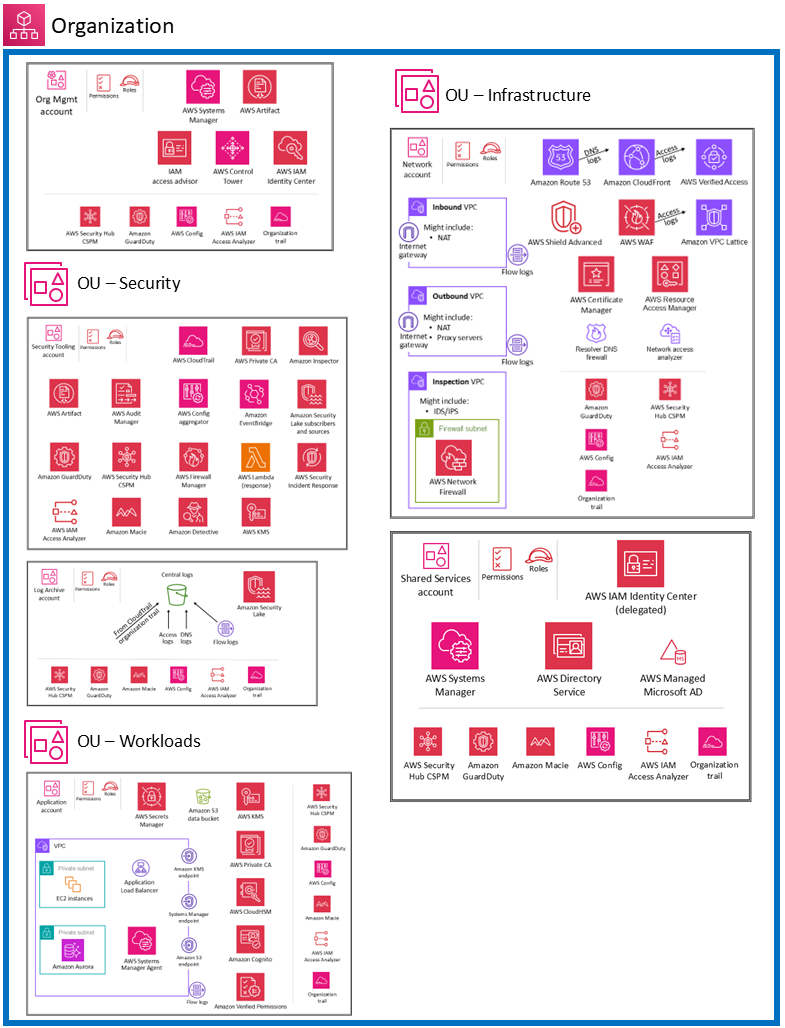
AWS Security Reference Architecture
For additional details on what a Reference Architecture for a secure environment looks like, review the following recommendation: