Permission GuardRails: Organizational Policies with SCPs and RCPs
Service Control Policies (SCP)
It is recommended to limit the maximum permission that can be granted by AWS IAM in your accounts at the organization level (or Org unit level), to enforce your security invariants (things you don’t want to allow in your organization and the rule doesn’t have frequent changes), These Permission Guardrails, can be enforced in AWS using Service Control Policies (SCPs). These policies do not grant any access, only limits the maximum effective permission.
SCPs can be applied to the whole organization, to a specific organizational unit or to a specific account:
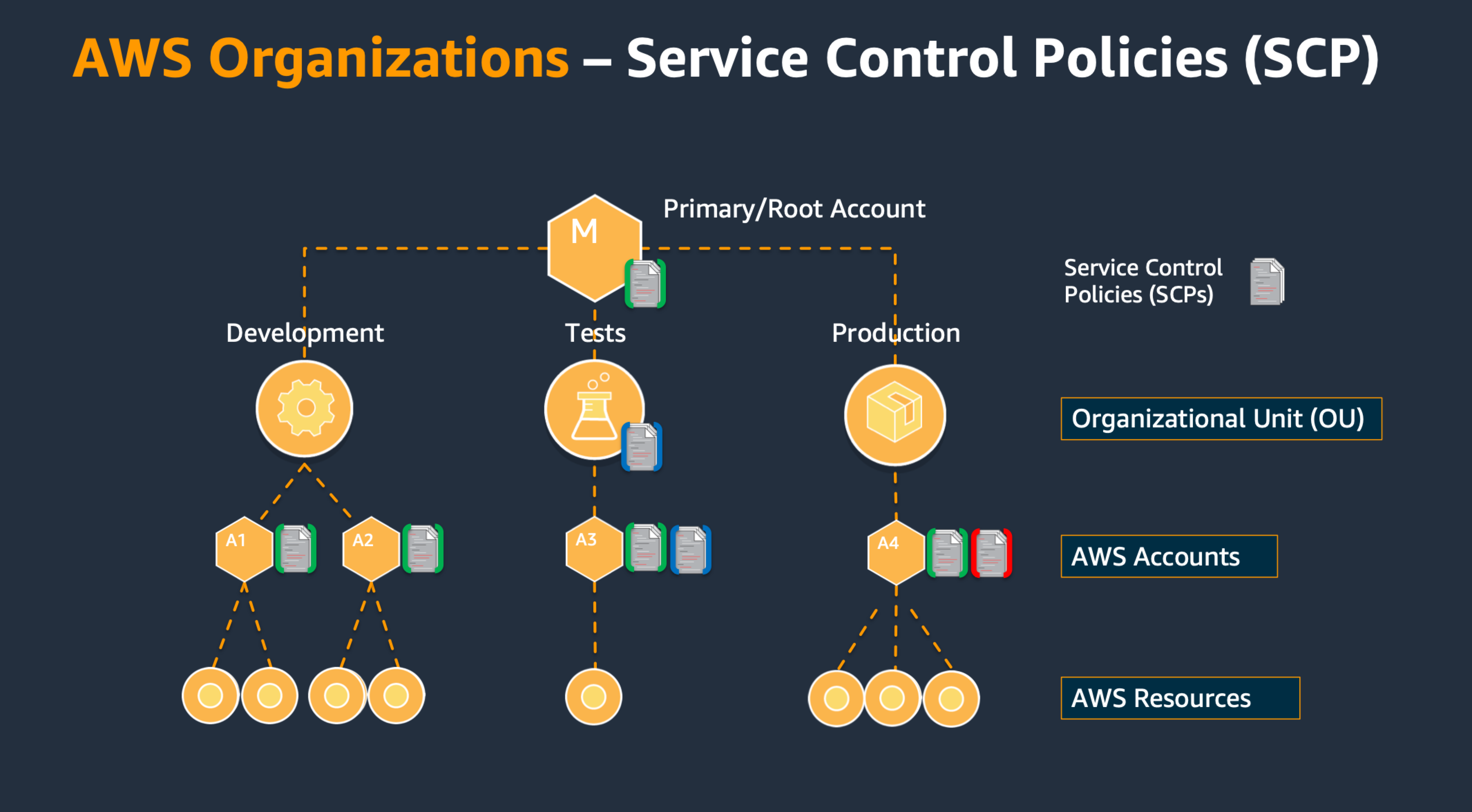
And SCPs will restrict the effective maximum permission:
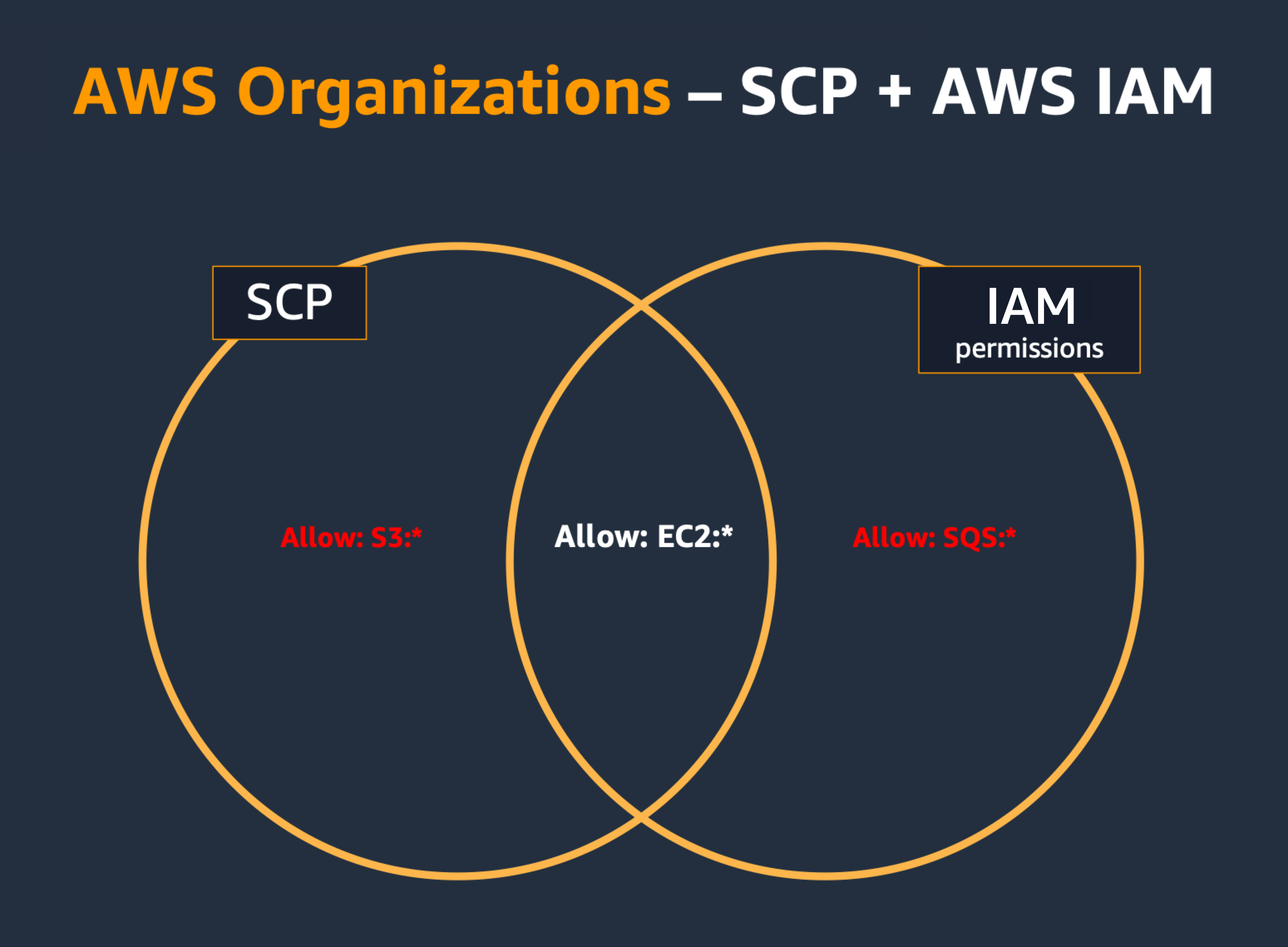
Therefore they are ideal to set up Security Invariants (the things that you want to set up and never change, or at least not frequently):
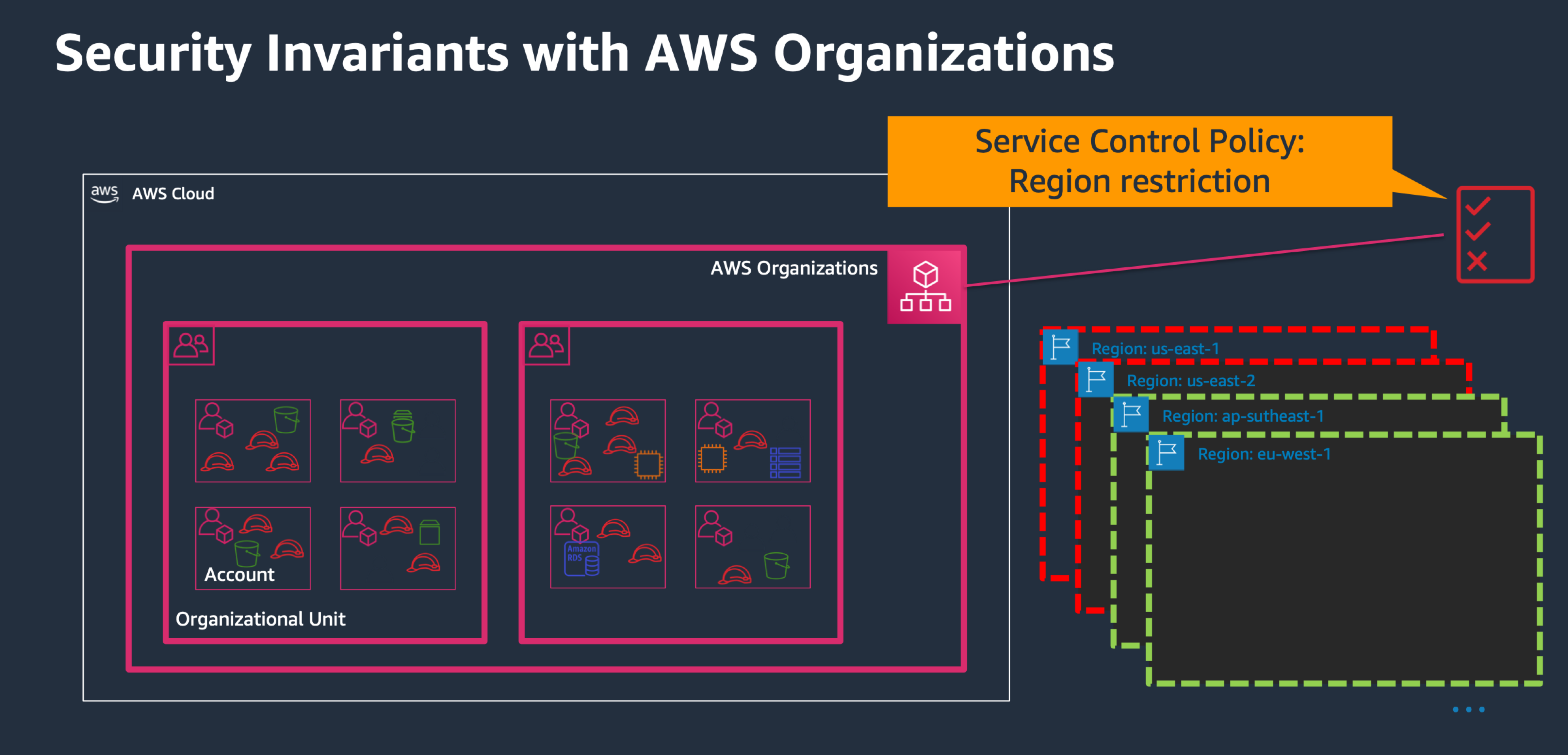
SCPs apply even the root user of the member accounts, but do not apply to the organizational management account (Organization root).
Service Control Policy (SCP) Examples
- SCP examples in AWS Documentation: https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_policies_scps_examples.html
- SCP examples GitHub repository: https://github.com/aws-samples/service-control-policy-examples
Resource Control Policies (RCP)
You can also apply a new type of permissions guardrail called Resource Control Policies (RCP). RCPs are resource-centric controls, that you can use to specify the conditions under which identities can access your resources centrally across resources in your organization. As SCPs, RCPs do not grant any permission, only limits the maximum permissions available for resources.
Think about everything that you never want it to happen in your accounts and enforce it through RCPs and SCPs.
Resource Control Policy (RCP) Examples
- RCP examples in AWS Documentation: https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_policies_rcps_examples.html
- RCP examples GitHub repository: https://github.com/aws-samples/resource-control-policy-examples
Well Architected Framework Recommendation Mapping
Risk Mitigation
- Incorrect permissions management can create undesirable results on IAM permissions increasing the impact of a compromised identity.
Guidance for assessments
- Are you leveraging SCPs & RCPs to enforce your security invariables ?
- Have you configured SCPs & RCPs to avoid undesirable actions such as these?:
- Prevent member accounts from leaving your organization ?
- Prevent the launch of very large instances on accounts other than production
- Prevent the use of instance types not aligned to your business needs (such as GPUs if you’re not doing AI/ML in that account or Organizational Unit)
- Prevent the use of root on member accounts ?
- Have you checked the SCP examples to see if any of those apply to your org?
Pricing
AWS Organizations is a free service. Service Control Policies are free to use.