Secure EC2 Instances Management
Manage your instances with AWS Systems Manager Fleet Manager
We recommend that you use AWS Systems Manager Fleet Manager or SSM Session Manager to manage your instances instead of directly accessing via SSH because you don’t need to open ingress ports in Security Groups, it allows MFA, and it provides command history auditing. In Windows instances, Fleet Manager allows you to gain access to Remote Desktop (RDP) as well.
While you can use hardened bastion hosts or third party tunneling solutions that limit the amount of exposed resources, it’s better to completely close the ingress to administration ports and leveraging the AWS Systems Manager agent to open an outgoing connection.
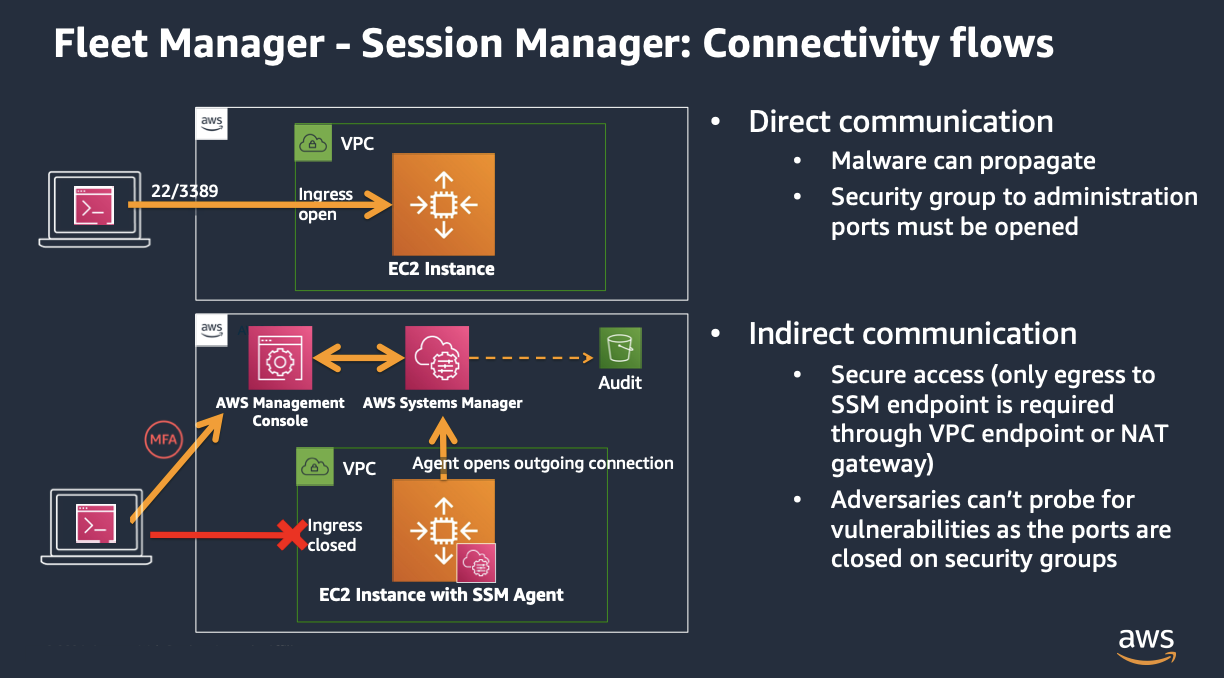
Fleet Manager is a free functionality within AWS Systems Manager, that requires the Systems Manager agent enabled. The agent is preinstalled in many AMIs
, but you still need to configure instance permissions required for Systems Manager
, adding the a role as IAM Instance Profile with the following managed policy: AmazonSSMManagedInstanceCore, and you need to provide network access to the ssm endpoint via a NAT Gateway or VPC Endpoint.
AWS Systems Manager Fleet Manager and Session Manager
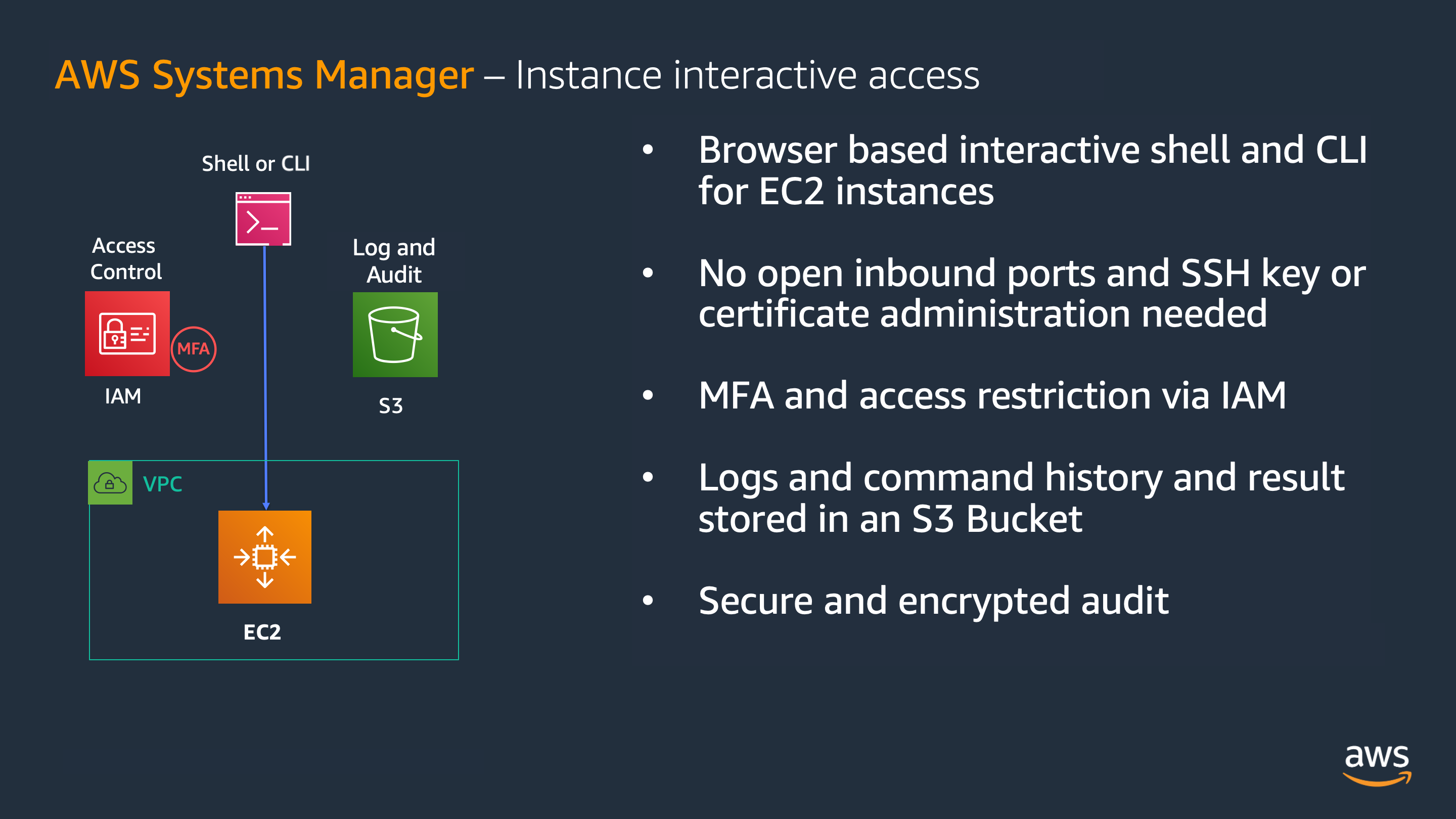
AWS Systems Manager (SSM) Session Manager allows you to connect to Unix/Linux instances or windows via Powershell instead of using SSH.
AWS SSM Fleet Manager provides several capabilities to manage instances (such as killing a process, upload/download a file without logging in to the instance) and provides connection to Windows instances using remote desktop. From Fleet Manager you can open a SSM Session Manager connections.
It’s possible to configure multi-factor authentication (MFA) for accessing to the console (on AWS IAM Identity Center or in the IAM user), and the service allows (optionally) to enable audit logs on the commands executed.
When using AWS Systems Manager Fleet Manager to connect to Windows instances you can authenticate using AWS IAM Identity Center, OS credentials or key pairs. Leveraging it’s integration with AWS IAM Identity Center you can log in to Windows instances with one click, and without providing additional credentials.
AWS SSM Session Manager
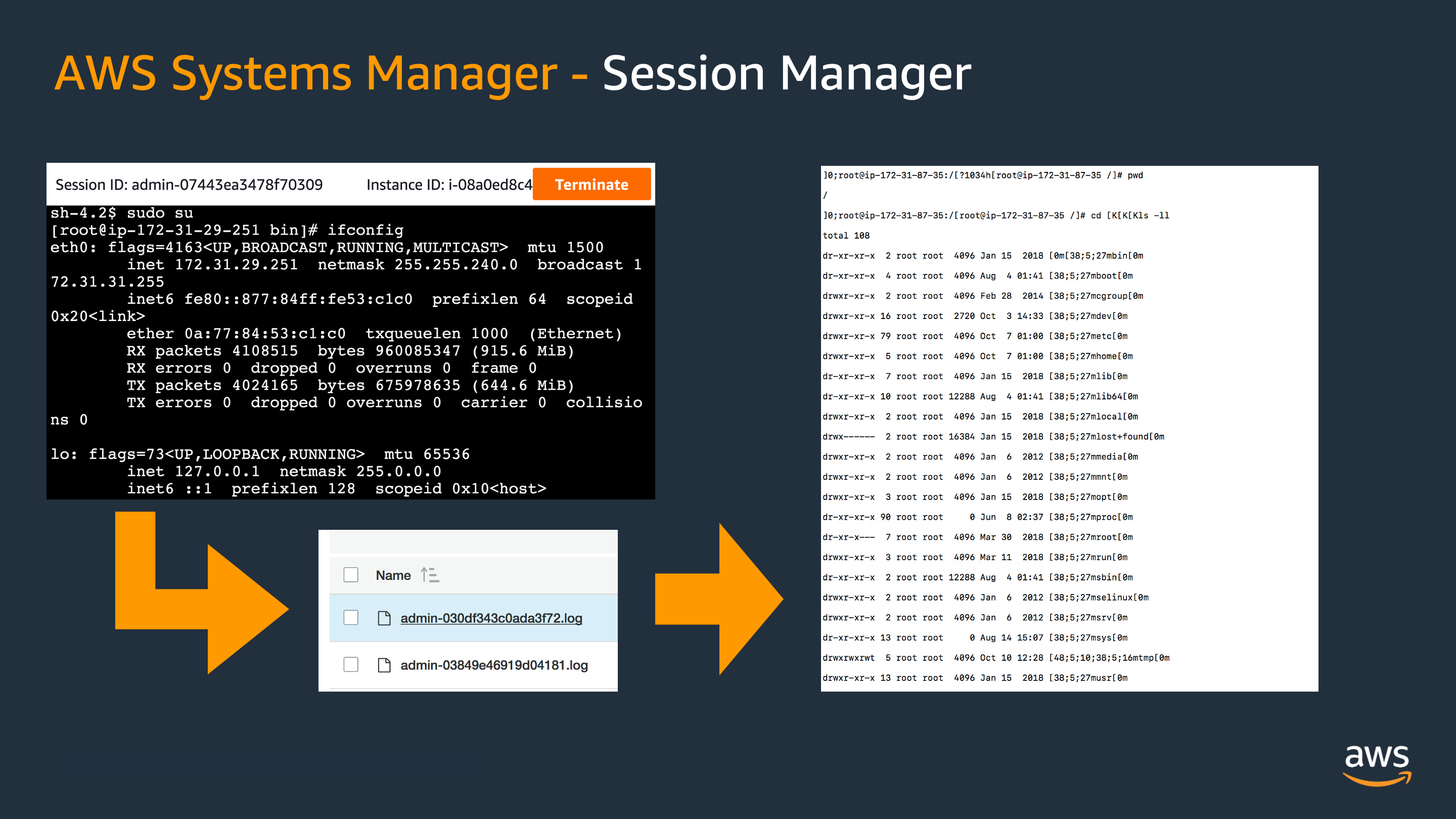
AWS SSM Fleet Manager Demo
Risk Mitigation
- Allowing unrestricted ingress access to administration ports (22 and 3389) is a significant risk, as often the hosts are not properly patched and hardened, as SSH and RDP BruteForce attacks are very common on open administration ports and vulnerabilities on these ports can grant access to an adversary.
Guidance for assessments
- Have you implemented the AWS Systems manager agent ? in what percentage of your EC2 instances in the organization ?
- Are your teams using Fleet Manager / Session Manager to manage instances ? percentage ?
- Have you removed admin ports from the security groups ?
Alternatives to Fleet Manager
There are multiple solutions for privileged access management (PAM) that provide you a logged shell on your instance, and often require you to provide network access to admin ports (22/3389) from that solution, if you decide to use these type of solutions, make sure you only allow access from that IP address.
Pricing
AWS Systems Manager Fleet Manager and AWS Systems Manager Session Manager have no additional cost.