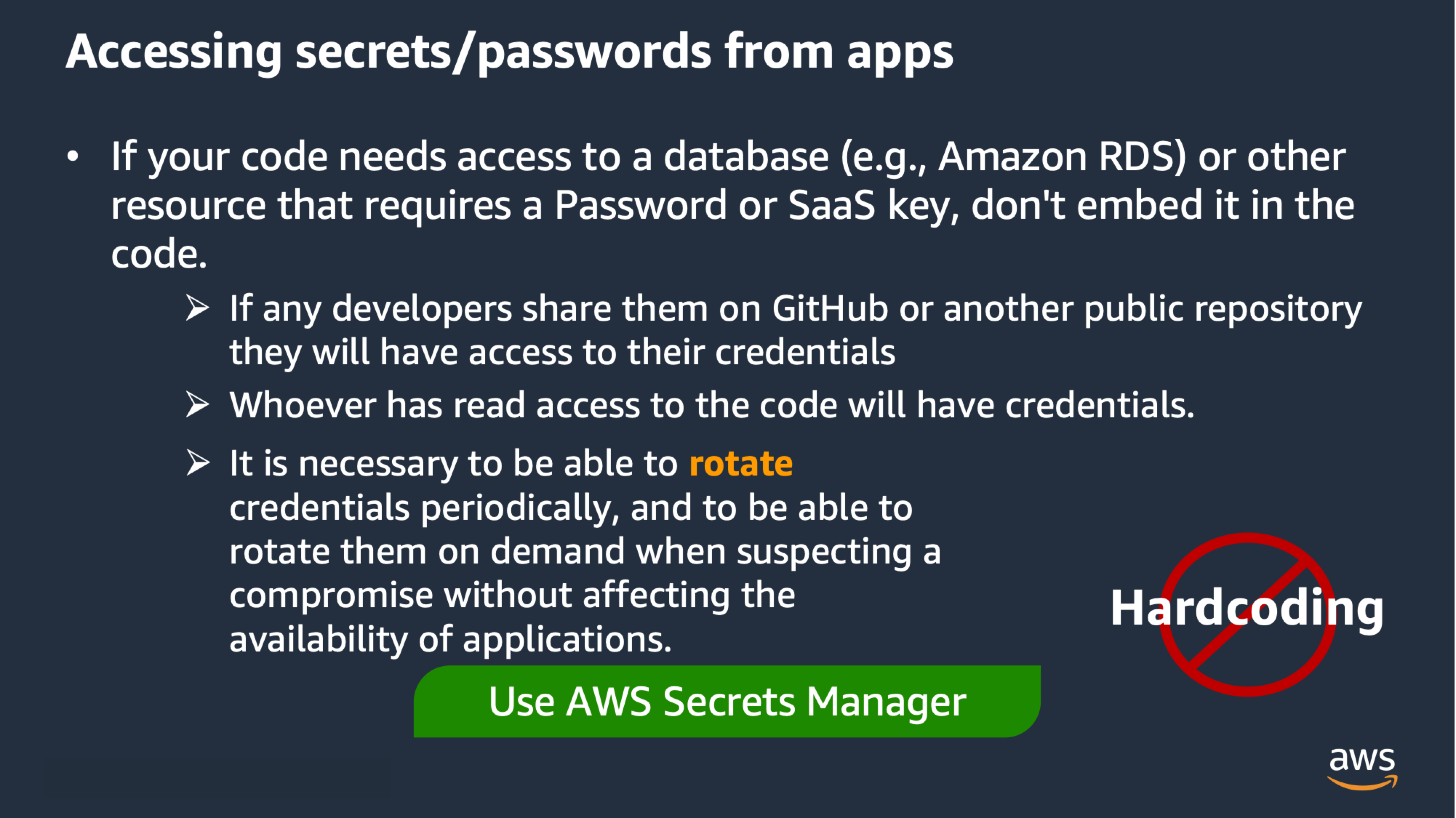
Don't store secrets in code - Remove secrets from code
Best Practice: Don’t hardcode Secrets in Code
Storing secrets in code is a mistake that may cause a credential to be unintentionally exposed.
If the hardcoded secrets are Access Keys, review the Use Temporary Credentials recommendation.
If you need to access from your code to some service that uses long-term credentials, leverage AWS Secrets Manager
to provide the credential when needed and handle rotation:
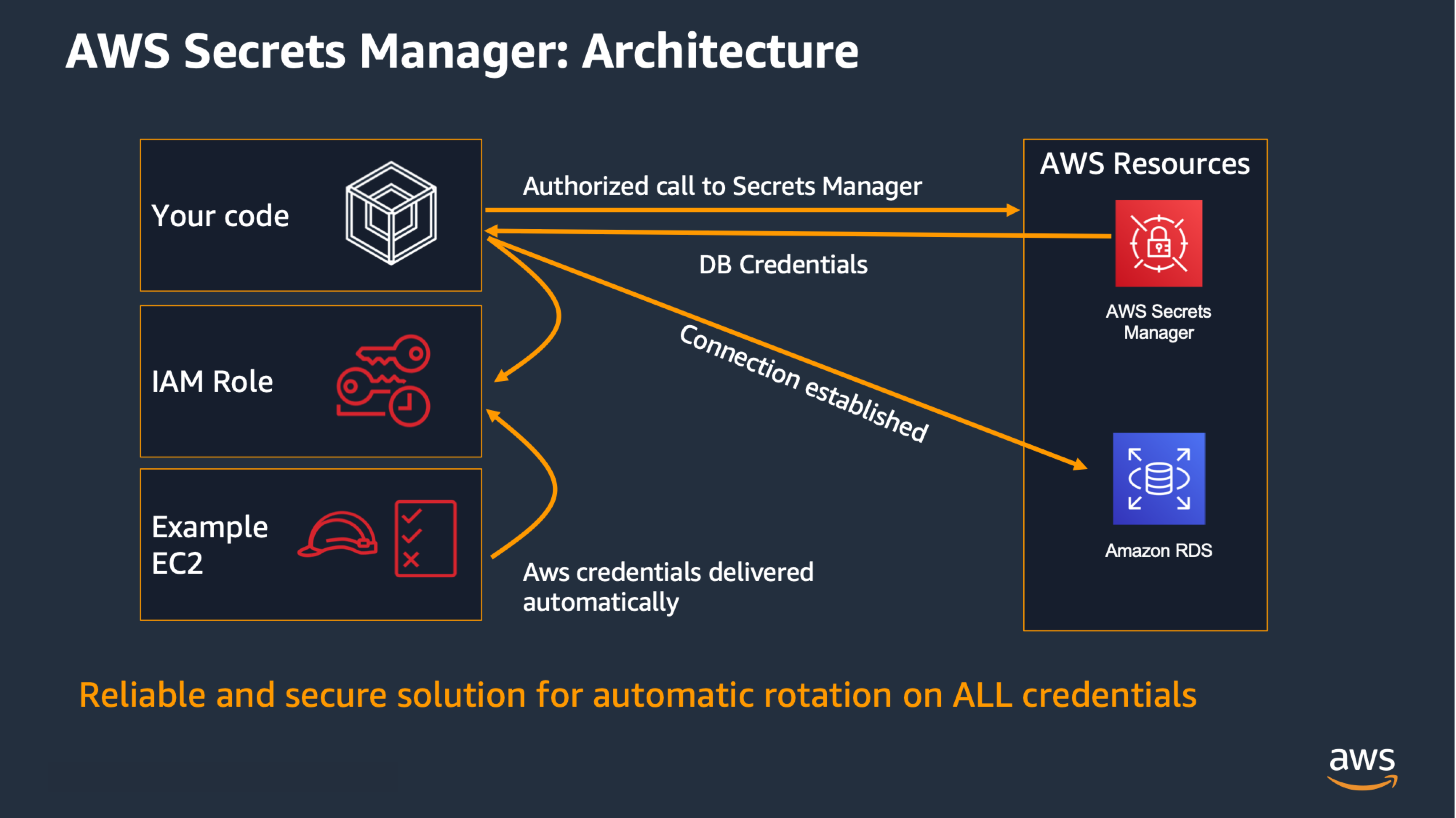
It works in a similar way to what is explained in the Use Temporary Credentials
recommendation, using Instance Profiles to get the permissions to check out a secret from AWS Secrets Manager, and then the application can retrieves the password and uses it to connect to the resource:
You can check your code with gitsecrets (opensource) to identify some secrets in code.
AWS Secrets Manager Best Practices
https://docs.aws.amazon.com/secretsmanager/latest/userguide/best-practices.html
Well Architected Framework Recommendation Mapping
- SEC02-BP05 Audit and rotate credentials periodically
Risk Mitigation
- If secrets (credentials - passwords/private keys/access keys) are stored in code, everyone that have read access to review the code (such as testers / reviewers) can grab those credentials and use it outside the code, or sell them to adversaries.
- Developers may share with the opensource community in open repositories such as GitHub and credentials may be exposed.
- Adversaries look for credentials such as Access Keys in open repositories.
- Hardcoded secrets are hard to rotate (particularly important in case of a known compromise where you need to rotate immediately).
- These risks also apply to secrets stored in config files on the same repository as the code.
Guidance for assessments
- Are you leveraging AWS Secrets Manager or a similar solution to store & rotate secrets such as Database passwords ?
- Are you controling that no secrets are stored in code ?
- Are your developers trained to understand that they should not be storing secrets in code ?
- Are your pipelines stopped when a secret is identified ?
AWS Secrets Manager videos
-
Back to basics: Secrets Manager
-
AWS Secrets Manager Demo
Pricing
https://aws.amazon.com/secrets-manager/pricing
You can try AWS Secrets Manager at no additional cost with a 30-day free trial. The free trial allows you to rotate, manage, and retrieve sensitive data for a period of 30 days.