Inventory & Configurations Monitoring
It is important to have an inventory of assets (at least at high level) of which applications are in each account, business process associated, and what type of resources they should have and significant security configurations that should be enforced. To maintain consistency on the alignment of security configurations to best practices it’s necessary to keep track of configuration changes in your assets. AWS has a service called AWS Config that monitors configuration changes, allows you to remediate undesirable configurations, or restore previous configurations thus correcting configuration deviations.
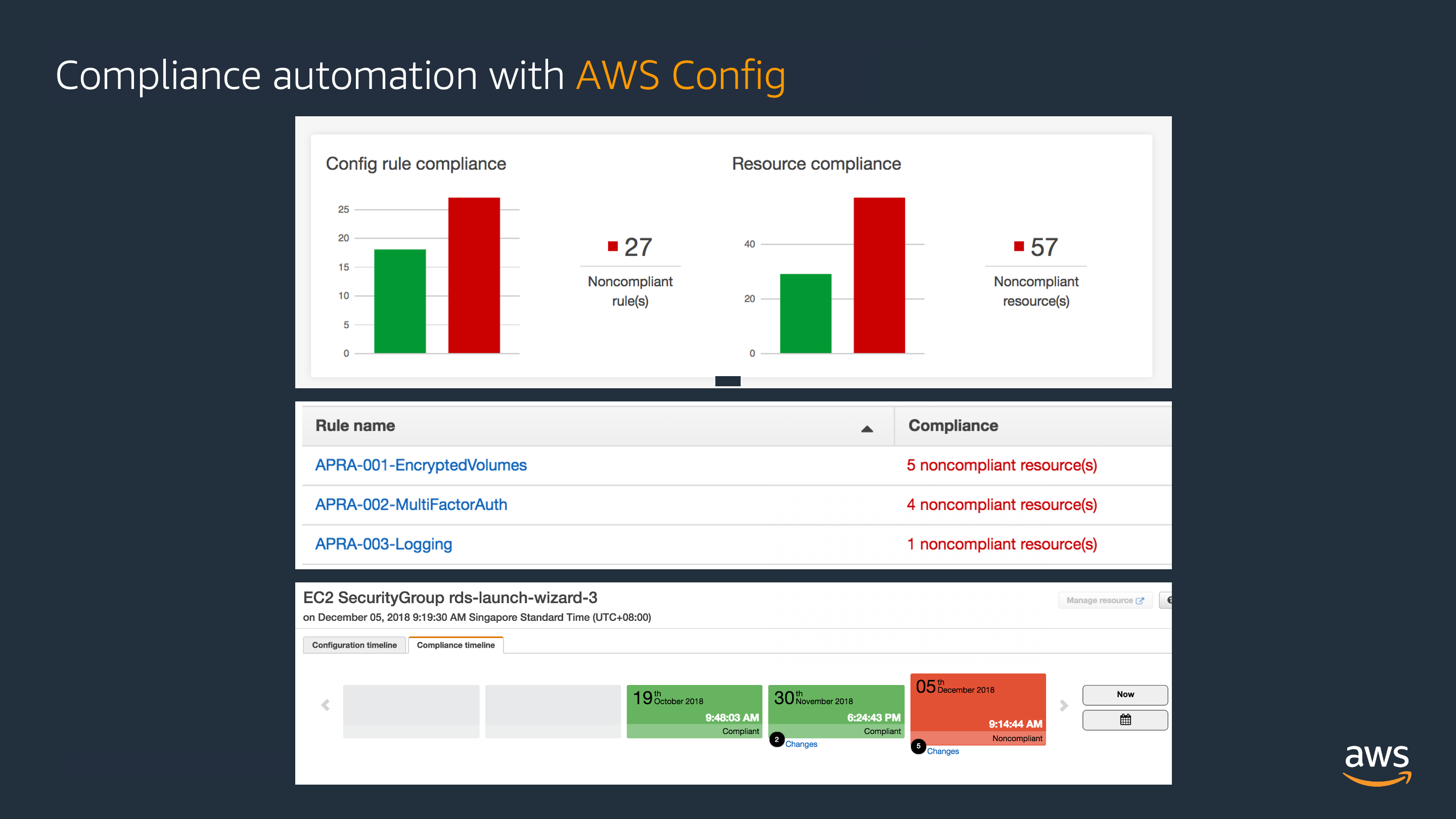
AWS Config Rules such as checking SSH or RDP ports opened to the world help strengthen the security posture significantly.
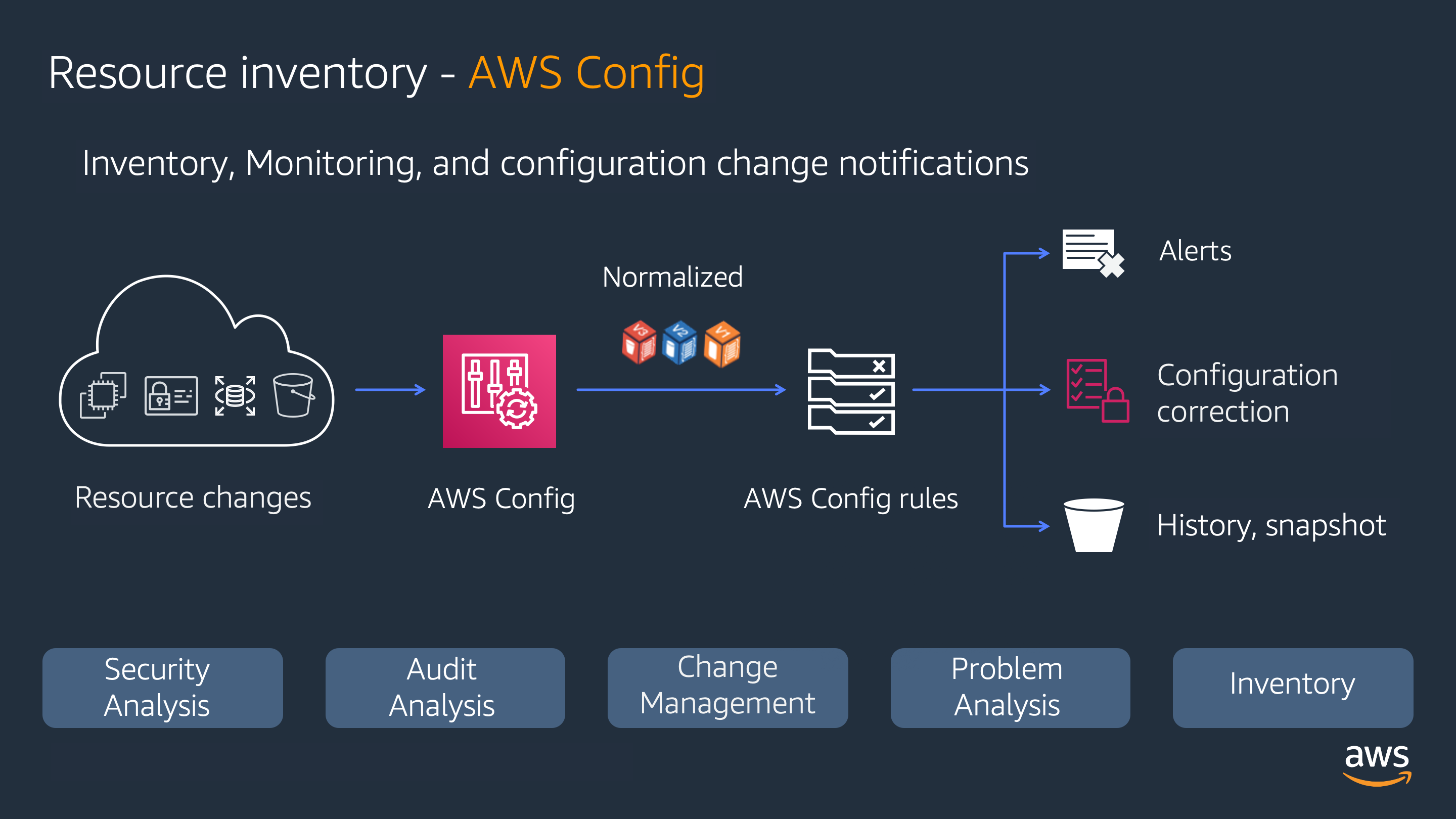
You can perform remediation actions that are based on AWS Systems Manager Automation Documents to identify, notify or correct resources that become non-compliant.
If you enabled AWS Control Tower , AWS Config will be configured automatically. AWS Security Hub security standards and AWS Firewall Manager require AWS Config to be enabled.
AWS Config Demo
AWS Config Mindmap
https://www.xmind.net/m/ACQQq3/
Risk Mitigation
- Without an inventory it’s harder to apply security controls, and also it’s harder to identify rogue assets created by adversaries.
- Tracking changes helps reducing misconfigurations.
Guidance for assessments
- Do you have an inventory of your assets ? (ideally including criticality, to which business process it’s related, accounts)
- Is AWS Config enabled in your organization ? (if you have AWS Control Tower, AWS Config is enabled when enabling Control Tower)
- Is your team trained on how to use AWS Config to detect what changed and when ? (particularly important for Incident response, can your team query resources or enable rules?)