Audit API calls
Enable, Centralize, and Secure AWS CloudTrail Logs
It is advisable to use AWS CloudTrail audit logs to investigate incidents by setting them to retain the logs for the period that your security policy determines.
AWS CloudTrail Event history is available for all customers for free to view online for 90 days without any additional configuration. You should take a look at these logs and learn how to search and understand your logs there. Cloudtrail logs older than 90 days are deleted by default, so you should configure Trails to send log output to an S3 bucket to retain these logs for a longer period.
It is also recommended to centralize them into a Logging account to protect them from malicious access and destruction, or if you use a single account, control access to those logs using IAM policies (but you should use an org if you have production workloads).
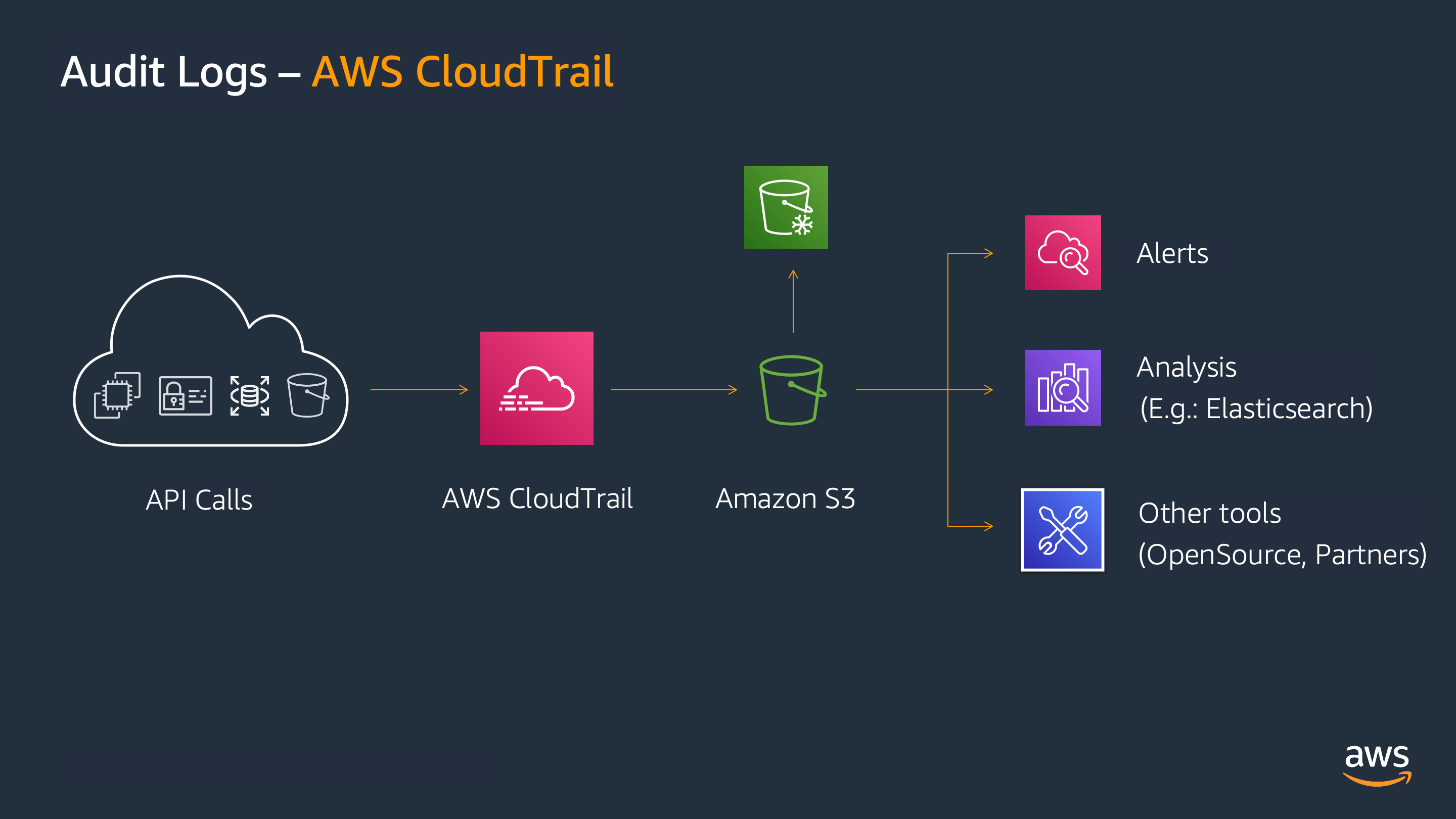
If you use AWS Control Tower for Multi-Account Management , the Logging account is generated, where the logs are automatically centralized and protected.
Your security team should be trained to understand how to search and investigate CloudTrail Logs.
AWS CloudTrail Mindmap
https://www.xmind.net/m/sY4HG3
Risk Mitigation
- Protecting the logs is crucial in security investigations to make sure you know what adversaries did and reverse their actions, removing any potential access.
Guidance for assessments
- Do you have AWS Control Tower enabled ?
- if not:
- Have you enabled CloudTrail organizational trail ?
- Have you enabled SCPs to prevent adversaries from stopping the generation of CloudTrail logs and manipulating the log files ?
- How prepared is your team to investigate CloudTrail logs ?
Pricing
https://aws.amazon.com/cloudtrail/pricing
Management event activity that AWS CloudTrail recorded during the last 90 days can be viewed and filtered for free through the AWS CloudTrail console or using the AWS CLI.