Block Public Access
Limit access to your Amazon S3 Buckets by using the S3 Block Public Access functionality
The S3 Block Public Access (BPA) feature allows you to block public access to all your Amazon S3 Buckets at the account level (in fact it is the default setting to avoid human errors) and at Bucket level. If your organization doesn’t need open buckets ensure that the Block public access is enabled at the account level for all accounts, and if an account requires an open bucket, ensure that all the buckets that do not need to be public are blocked.
Only by removing the lock is possible to publicly share data from a bucket (for example to create a static website). This block invalidates Bucket policies.
There is a visual marker with a yellow background and the word Public next to the bucket when you have a policy that allows public access.
You can read more about the subject in the AWS Blog
It’s advisable to use Service Control Policies to prevent the removal of the Block Public Access if it’s not needed.
If you have many accounts you can use AWS Security Hub’s S3.1 control to see which accounts don’t have the BPA enabled, and S3.8 to validate whether BPA is enabled at bucket level.
Enable Block Public Access for AMIs and EBS Snapshots
We recommend you to block public access on AMIs and to block public access on EBS Snapshots unless you really have a valid use case for it.
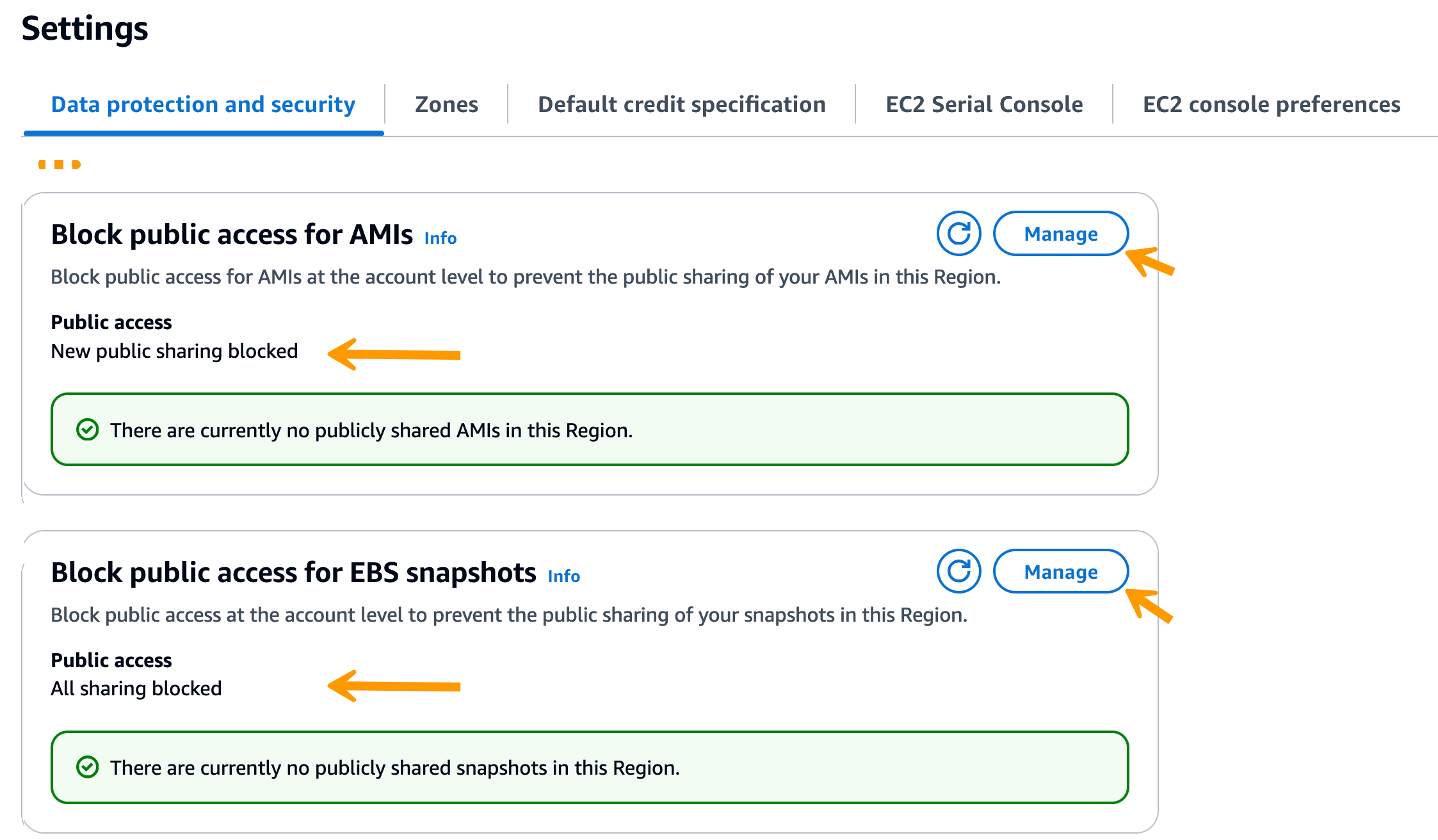
How to check
- AWS Security Hub security standards:
Risk Mitigation
- [Exfiltration] - Users may misconfigure Amazon S3 buckets opening them for public access.
Guidance for assessments
- Do you have Amazon S3 Block Public Access enabled at account level in all the accounts in your organization ?
- Have you enabled BPA for EC2 AMIs and Amazon EBS ?
- Have you enabled SCPs to prevent the removal of the BPA ?
If you need buckets to be public:
- What is your use case ? is that a public static website ? Why not protecting that data with an Amazon CloudFront distribution with AWS WAF rules enabled?
- Are there any public buckets that you do not have identified that they absolutely need to be public?
- If there are some public buckets: have you block public access at the bucket level for all other buckets in the account ?
Pricing
There’s no additional charge for enabling Block Public Access