Perímetros de datos de IAM: Acceso Condicional
NOTA: La versión en Inglés cuenta con algunas actualizaciones que aún no se reflejaron en la versión en español.
A medida que las organizaciones amplían su presencia en la nube e intentan alcanzar mayores niveles de agilidad empresarial mediante la adopción de un enfoque descentralizado para las operaciones en la nube, buscan formas de prevenir los riesgos asociados con errores de configuración y acceso no deseado a sus datos. Los perímetros de datos en AWS (En inglés) son uno de los mecanismos que hemos visto que las empresas utilizan con éxito para reducir estos riesgos y mejorar la postura de seguridad de sus entornos de nube de múltiples cuentas.
Definiciones de perímetro de datos
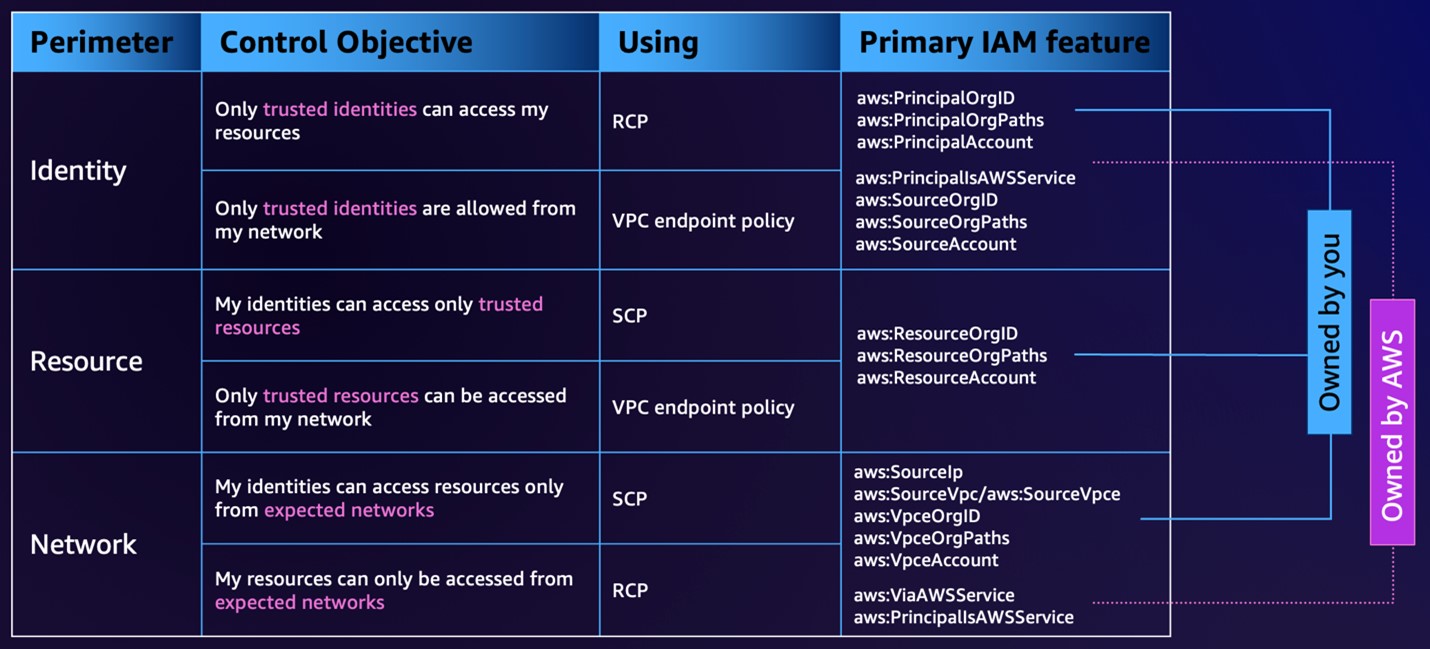
Un perímetro de datos es un conjunto de barreras de seguridad de permisos que ayudan a garantizar que solo las identidades confiables accedan a los recursos confiables de las redes esperadas. Las barreras de seguridad del perímetro de datos están diseñadas para funcionar como límites siempre activos para ayudar a proteger los datos de los clientes en un amplio conjunto de cuentas y recursos de AWS. Estas barreras de seguridad para toda la organización no reemplazan los controles de acceso de grano fino. En cambio, ayudan a avanzar a través del recorrido de privilegios mínimos de una manera más ágil al aplicar invariantes de seguridad.
- Identidades confiables: Principals (roles o usuarios de IAM) dentro de sus cuentas de AWS o servicios de AWS que actúan en su nombre.
- Recursos confiables: Recursos propiedad de sus cuentas de AWS o de servicios de AWS que actúan en su nombre.
- Redes esperadas: Sus centros de datos locales y nubes privadas virtuales (VPC), o redes de servicios de AWS que actúan en su nombre.
Objetivos de control en perímetro de datos
Recorrido por el perímetro de datos
Los controles del perímetro de datos deben tratarse como cualquier otro control de seguridad dentro del programa de seguridad de la información y gestión de riesgos. Esto significa que debe realizar un análisis de amenazas para identificar los riesgos potenciales dentro de su entorno de nube y, luego, en función de sus propios criterios de aceptación de riesgos, seleccionar e implementar los controles del perímetro de datos adecuados. Para fundamentar mejor el enfoque iterativo basado en riesgos para la implementación de los controles del perímetro de datos, debe comprender qué riesgos de seguridad y vectores de amenazas aborda el marco del perímetro de datos, así como sus prioridades de seguridad.
Control de acceso en capas mediante múltiples políticas que aprovechan el contexto
Se recomienda aplicar el control de acceso basado en riesgos para aplicaciones críticas de múltiples capas para garantizar que no haya errores de configuración que dejen recursos expuestos, para limitar el acceso solo desde donde esperamos que lleguen los accesos y solo a los objetivos mínimos requeridos.
AWS almacena información útil para usar en condiciones de IAM dentro de la sesión, de modo que pueda otorgar acceso en las circunstancias adecuadas.
Criterios como si la solicitud proviene de un rango de IP o si se invoca desde una cuenta dentro de su organización son condiciones que puede adjuntar a las políticas de IAM.
Workshop
Mitigación de riesgos
- Los errores de configuración en IAM o en las políticas basadas en recursos pueden dejar los recursos expuestos a un acceso no deseado.
- Divulgación no deseada de datos a través de credenciales no corporativas o robadas.
Guía para evaluar su grado de alineación
- ¿Está aprovechando los perímetros de datos para proteger sus aplicaciones críticas?
- ¿Ha implementado Resource Control Policies (RCP) para evitar el acceso a sus recursos desde fuera de su organización?
- ¿Está controlando con las condiciones de IAM que el acceso a las aplicaciones y recursos críticos (como los buckets S3) SOLO se permita desde donde se espera?
Precios
El servicio AWS IAM es gratuito y la configuración de políticas de recursos (como políticas de bucket) no tiene ningún costo adicional.